Extortion for Xmas: The 35th anniversary of ransomware
Toasting the unlikely birth of an illicit industry that now turns over more than $1 billion each year.

Criminals are a uniquely inventive bunch. Just think of credit card skimmers, scams like the Ponzi scheme, the submarines cartels use to smuggle cocaine or any number of dastardly innovations. Clever crooks have brought a lot of new ideas into the world.
So it's with a bitter heart that we toast the 35th anniversary of one of the underworld's most profitable ideas: ransomware.
The first ransomware virus was unleashed before the rollout of email and was delivered on floppy disk by post or hand to 20,000 attendees of the World Health Organisation’s (WHO) AIDS conference in Stockholm in December 1989.
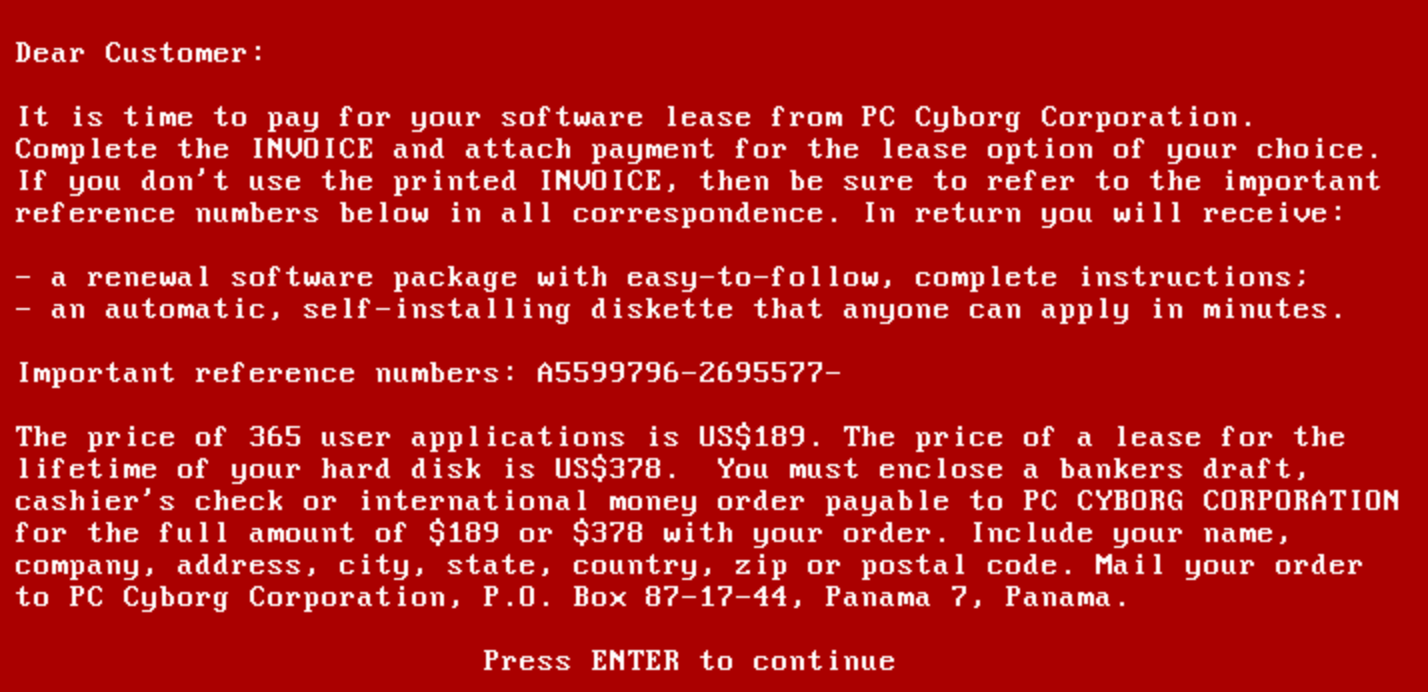
Whilst this “AIDS Information Introductory Diskette" looked innocent, it contained a Trojan called the Aids Info Drive or PC Cyborg Trojan.
Once installed, the AIDS Trojan replaced the system’s AUTOEXEC.BAT file, a critical MS-DOS startup script. This modification allowed the program to track how many times the computer had been booted. After 90 boots, the Trojan activated, hiding directories and encrypting the names of all files on the main harddrive, rendering the system unusable.
Users were then presented with a ransom demand, instructing them to “renew the license” by contacting PC Cyborg Corporation. The payment, set at $189, had to be sent to a post office box in Panama, making this one of the earliest examples of financially motivated cybercrime.
Cybercrime and punishment: The fate of the first ransomware scammer
Dr. Joseph Popp, the creator of the AIDS Trojan, was eventually identified and arrested. He was detained in Brixton Prison after being charged with eleven counts of blackmail.
Despite clear evidence linking him to the ransomware, Popp defended his actions by claiming that the money collected by the PC Cyborg Corporation was intended for AIDS research. As a Harvard-trained anthropologist, Popp had ties to humanitarian organisations like the Flying Doctors, a branch of the African Medical Research Foundation (AMREF), and served as a consultant for the WHO in Kenya, where he helped organize a conference for the Global AIDS Program.
Popp acted strangely and erratically after his arrest during a routine baggage inspection at Amsterdam Schiphol Airport. He was later declared mentally unfit to stand trial and was returned to the United States.
Kevin Curran, senior member of the the Institute of Electrical and Electronics Engineers (IEEE) and professor of cybersecurity at Ulster university, told Machine about how ransomware has evolved since that fateful first IRL attack.
"Whilst threat actors have changed their tactics, their motives remain the same – money and disruption," he said. "Ransomware to this day, is one of the biggest cybersecurity threats to enterprises. Threat actors have gone to a great effort to remain under the radar and bypass even the strongest security protocols. Some have adopted a 'radio silence' technique, through a sophisticated monitoring of system processes, where malware knows when to stay silent or lie dormant; 'stealth mode' techniques have been adopted by malware to evade detection."
How much of a threat is ransomware?

Ransomware has now turned into a major industry. In 2024, an unidentified company paid a record-breaking $75 million ransom to the Dark Angels ransomware group. In 2023, ransomware payments reached a record high, exceeding $1 billion for the first time.
So how have things changed since the days of malicious floppies?
“With the earlier forms of ransomware, the impact was downtime or unavailable data. Now there are far more aggressive strains; double or even triple-extortion tactics. Seven years ago, WannaCry became one of the first examples of a worldwide cyber-attack, ultimately establishing ransomware as a major cyber threat vector," Curran added.
"Then there was of course, the 2021 attack on the Colonial pipeline in the USA, which revealed the damage ransomware can pose to critical national infrastructure (CNI) as it disrupted an asset which controls 50 percent of the fuel supply in North America.
“Sadly, cybercrime has steadily become an industry where some groups have cybercrime units typical of any large legitimate business, such as partner networks, associates, resellers and vendors. In fact, they even have dedicated call centres which are typically used to help with requests from ransomware victims. Ransomware-as-a-service (RaaS) has also become more prominent now, where threat actors offer franchises – predeveloped ransomware or malware in the form of ‘pay-for-use’ – or even training.
“There are also new ‘masterminds’ . Black Cat, LockBit, Cl0p, Revil and Conti are main ransomware groups at the moment, each have their own tactics and are responsible for conducting some of the most devasting attacks; they are constantly refining their methods to enhance their effectiveness and reach. Sadly, the question is no longer ‘if’ an organisation will be targeted, but when.
"Organisations must adopt a ‘secure-by-design’ methodology and follow the advice from authorities like the UK's National Cyber Security Centre (NCSC) ensuring that they adopt the most robust cybersecurity measures to mitigate these risks."
Have you got a story to share? Get in touch and let us know.




