VanHelsingRaaS ransomware vampires bite their first victims
It's named after Dracula's nemesis - but the new ransomware-as-a-service program is just as much of a bloodsucker as the famous count.

Check Point Research has issued a warning about a new ransomware-as-a-service (RaaS) threat named after a famous fictional vampire hunter.
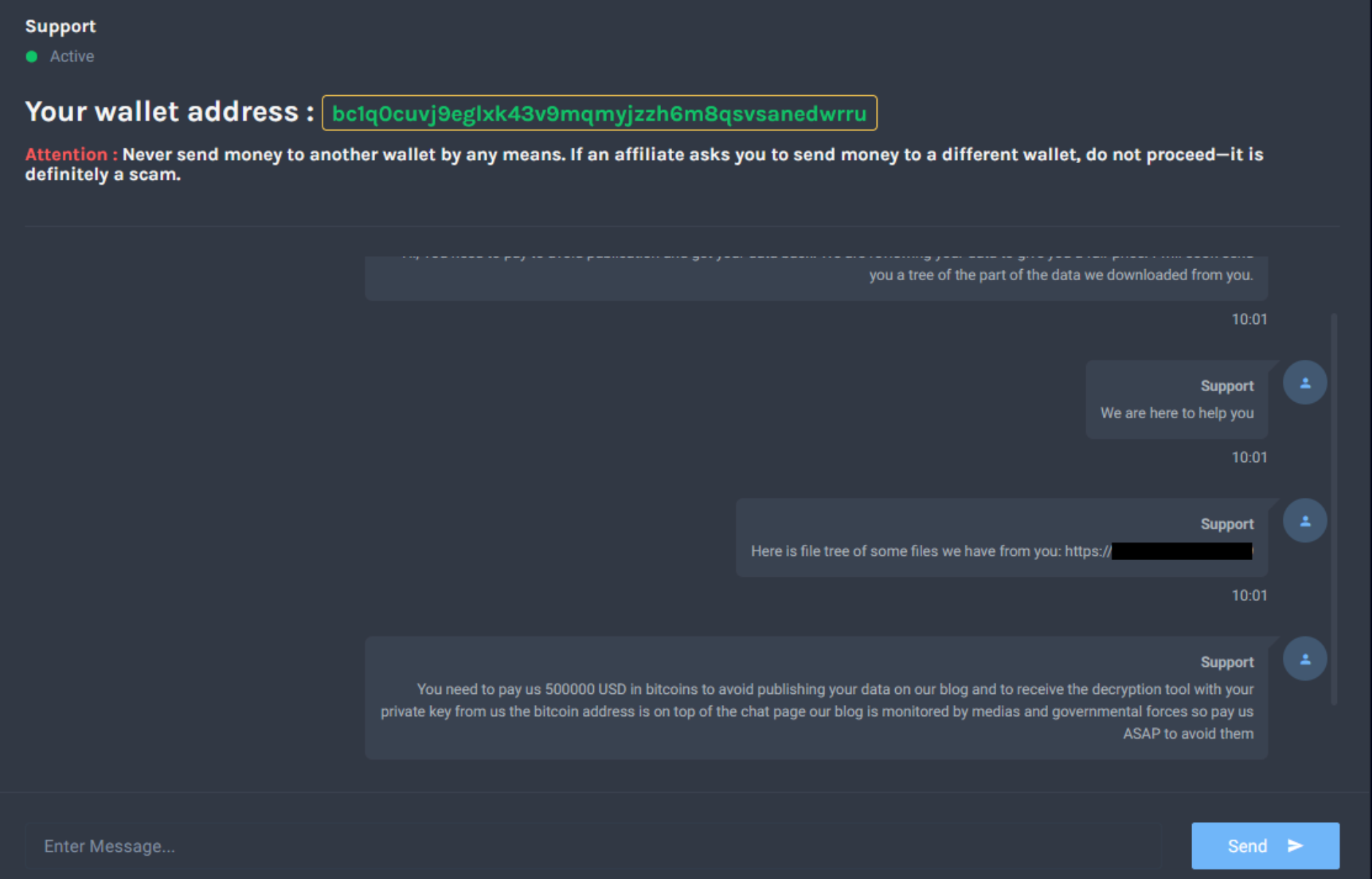
VanHelsingRaaS is a "new and rapidly growing" RaaS affiliate program launched on March 7, 2025. One actor has already demanded $500,000 in Bitcoin from their target in exchange for decryption keys and the deletion of stolen data.
The RaaS program allows "a wide range of participants", from new blood to seasoned hackers, to launch campaigns.
"This service has already demonstrated its rapid growth and deadly potential, having infected three victims within just two weeks of its introduction," Check Point wrote.
The criminal scheme appears to be inspired by Abraham Van Helsing, a famous character who rammed a stake into the heart of the eponymous hero of Bram Stoker's famous novel, Dracula.
Its moniker may also be based on a 2004 film called Van Helsing, which did not enter the artistic canon in quite the same way as the seminal text because, well, it was rubbish.
Lowering the barrier of entry for ransomware scammers
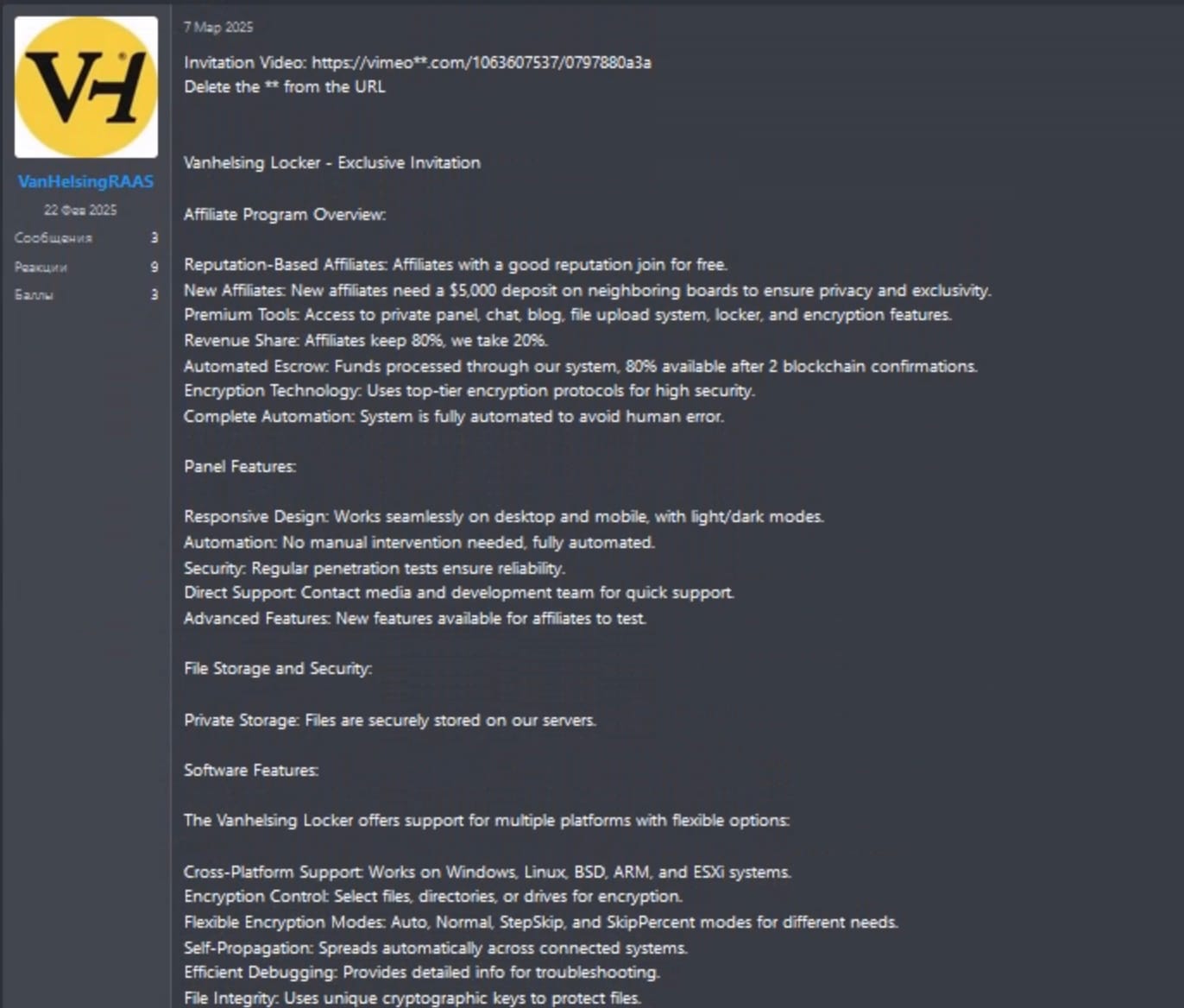
Anyone can join VanHelsing and start earning money from extortion. Unknown would-be hackers have to pay a $5,000 deposit, while experienced crooks can get access for free.
Affiliates get to keep an 80% stake (sorry) of the ransom payments while the core operators earn 20%. The only rule they must follow is to avoid targeting the Commonwealth of Independent States (CIS), a group of nations centred around Russia. More on that point later.
Check Point Research discovered two VanHelsing ransomware variants targeting Windows. However, in an advertisement, the RaaS gang said it could provide other versions "targeting Linux, BSD, ARM, and ESXi systems".
Would-be ransomware scammers can take advantage of an "intuitive control panel that simplifies operating ransomware attacks".
Check Point Research obtained two variants of the VanHelsing Ransomware, which were compiled just five days apart.
"The newest variant shows significant updates, highlighting the fast-paced evolution of this ransomware," it added.
"This multi-platform support significantly broadens the reach of the ransomware, enabling it to target a wide variety of systems. In addition to the locker, affiliates are provided with a dedicated control panel that facilitates the management and execution of ransomware campaigns."
Fangs for paying the ransom...
The ransomware was first identified on March 16, 2025. It is written in C++, and based on its compilation timestamp, it was likely deployed the same day against its first victim. The malware accepts multiple command-line arguments that control how encryption is carried out, including targeting network drives, local files, and specific directories.
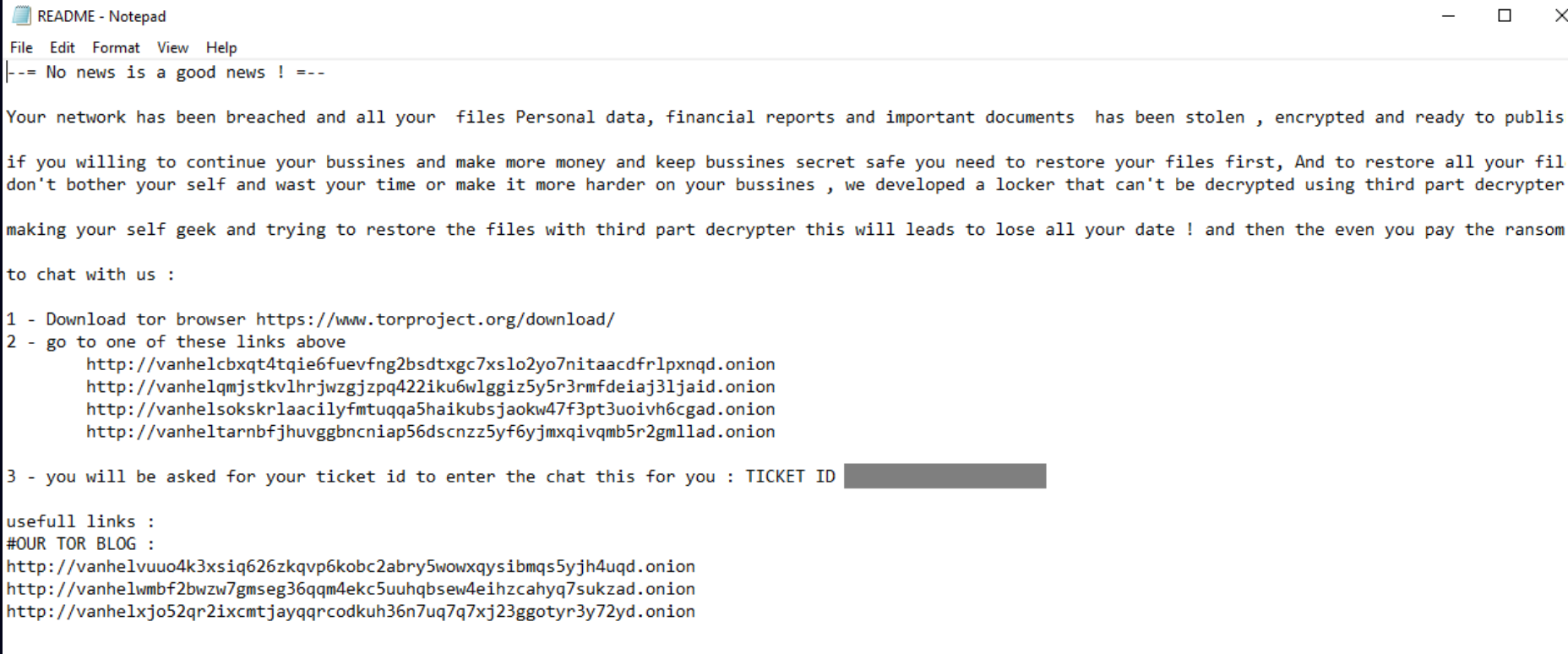
The ransom note, dropped as a README.txt file in affected directories, informs victims that their data has been encrypted and warns against using third-party decryption tools. It states that the only way to recover files is by paying the ransom and contacting the attackers.
VanHelsing drops two images on infected systems: one to change the desktop background and another intended to associate with encrypted files. However, the ransomware mistakenly uses a .vanlocker extension for this association, while the actual encrypted files use the .vanhelsing extension.
The ransomware also contains a PDB file path that reveals information about its development environment.
Researchers from Check Point discovered two additional related files, including a second VanHelsing variant compiled on March 11, 2025. One file is an updated version of the ransomware, while the other is a loader that attempts to deploy an embedded binary but fails due to a missing payload.
The ransomware is still under development, with several incomplete features noted in the code.
Check out Check Point's blog for full IoCs.
The rise of RaaS and a forbidding ransomware threat landscape
The cybersecurity firm Field Effect said VanHelsing "is not the only new RaaS operation making headlines this month".
A group called SuperBlack has also unleashed two "new, aggressive ransomware actors" in March 2025.
"VanHelsing’s business model reflects a growing trend among cybercriminal enterprises: lower barriers to entry and more lucrative payouts for affiliates," the Field Effect Security Intelligence Team wrote.
"Several recent RaaS groups have shifted towards incentivizing affiliates with lower fees and higher revenue splits, making it easier and more financially beneficial for more cybercriminals to join their ranks. For example, groups like BlackCat/ALPHV, LockBit 3.0, and Ragnar Locker, have all increased affiliate payouts to 80-90% in recent years.
"One of the most telling signs of VanHelsing’s origins is its explicit rule prohibiting attacks against the Commonwealth of Independent States (CIS). This is a hallmark of ransomware groups, such as LockBit, Conti, and REvil and BlackCat/ALPHV, as many cybercriminal organizations in the region maintain an informal agreement with Russian authorities to not attack domestic targets and provide a portion of their profits in exchange for authorities to look the other way.
"The Russian government’s lax enforcement against these groups has long been a point of geopolitical tension, especially following the Colonial Pipeline ransomware attack by DarkSide in 2021 and the subsequent REvil supply chain attacks. Even when the FSB arrested members of REvil in early 2022, many experts speculated that it was more about political manoeuvring than a genuine crackdown."
The researchers said the emergence of VanHelsing is a chilling reminder that ransomware is getting cheaper, easier to deploy and more expensive for victims.
"By lowering the cost of entry, expanding cross-platform targeting, and keeping more of their operations in the shadows, groups like VanHelsing are making ransomware even more accessible to criminals worldwide.
"As long as countries like Russia continue to provide safe havens for these groups, the ransomware-as-a-service model will remain a formidable threat to organizations everywhere."
Have you got a story or insights to share? Get in touch and let us know.