UK critical national infrastructure ransomware payment ban risks creating an "underground economy"
Westminster wants to make CNI and public sector bodies "unattractive" to criminals - a plan that could have an unexpected effect.

The UK government has put forward proposals to ban critical national infrastructure (CNI) organisations from making ransomware payments.
A new strategy aims to “strike at the heart of the cybercriminal business model” by prohibiting all CNI and public sector bodies, including NHS, schools and local councils, from bowing to criminals' demands.
It’s hoped that removing the financial incentive will make public sector targets “unattractive” to ransomware gangs.
However, it's feared that the plan could help create and nourish a dark underground market that enables organisations to break the law and make ransomware payments illegally to end the pain of an ongoing attack.
Dan Jarvis, Security Minister, said: “Driving down cybercrime is central to this government’s missions to reduce crime, deliver growth, and keep the British people safe.
“With an estimated $1 billion flowing to ransomware criminals globally in 2023, it is vital we act to protect national security as a key foundation upon which this government’s Plan for Change is built.
“These proposals help us meet the scale of the ransomware threat, hitting these criminal networks in their wallets and cutting off the key financial pipeline they rely upon to operate."
The Moscow connection: Russia's ransomware gangs at the centre of an international crimewave

The Home Office said Russia-affiliated criminal gangs are responsible for the lion’s share of ransomware attacks and warned they “continue to pose the most immediate and disruptive threat to the UK’s critical national infrastructure”, according to the National Cyber Security Centre’s (NCSC) Annual Review 2024.
“They also cause more disruption and pose a greater risk than other cybercrimes,” the government wrote.
Recent cyberattacks have included a key supplier to London Hospitals and Royal Mail, with "devastating impacts on the public".
Proposals for protecting CNI and the public from ransomware
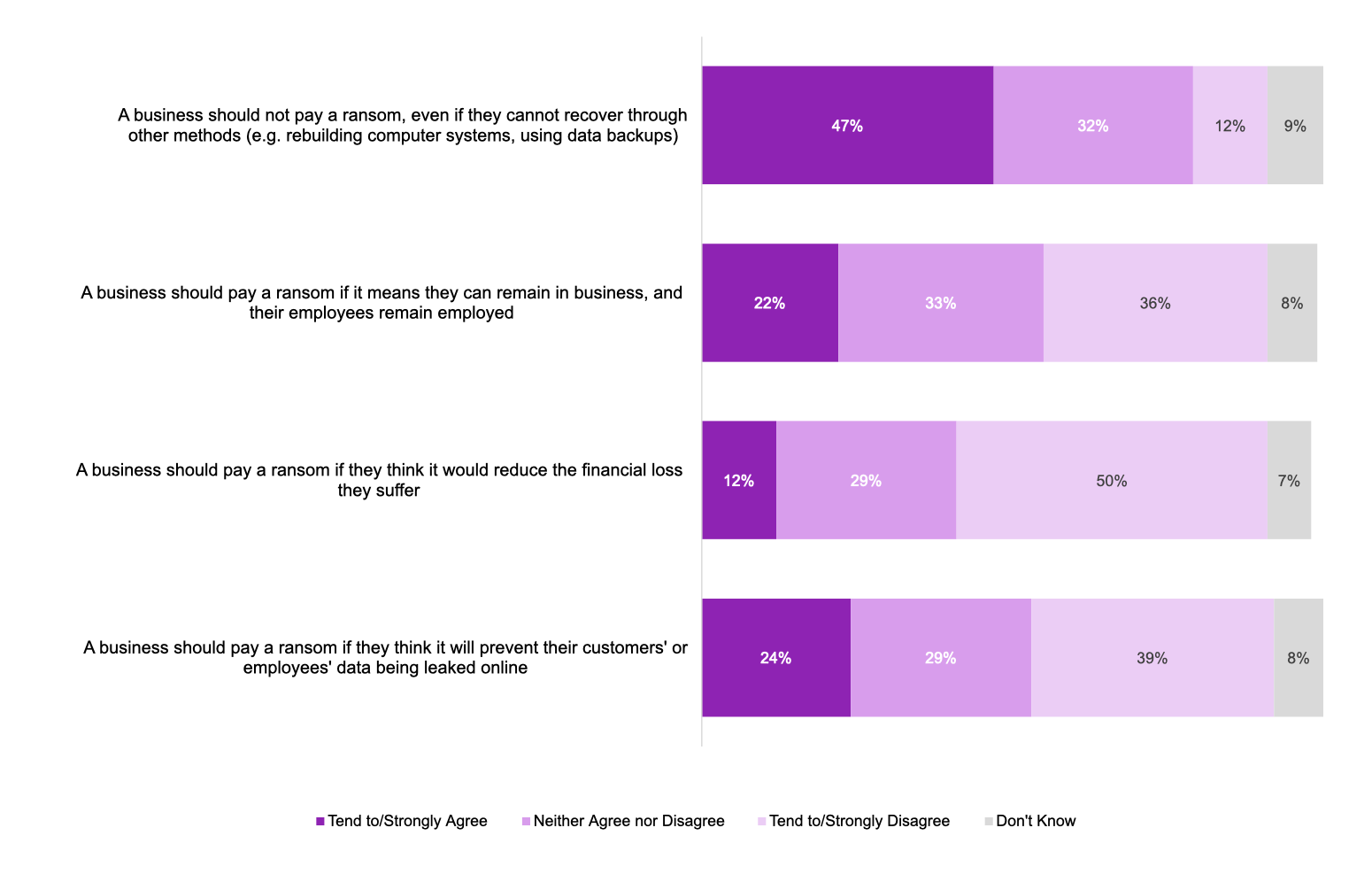
The Home Office-led consultation will consider three proposals:
Extending the ban on ransomware payments: Introduce a targeted prohibition on ransomware payments for public sector bodies and critical national infrastructure, building on the existing restrictions for government departments. This measure aims to deter ransomware attacks on the essential services the UK depends on by making them less appealing targets for cybercriminals.
Implementing a ransomware payment prevention regime: Strengthen the National Crime Agency’s ability to respond to ransomware incidents by increasing awareness of active attacks and ransom demands. This initiative will provide victims with expert advice and guidance while enabling mechanisms to block payments to known criminal groups and sanctioned entities.
Establishing mandatory reporting for ransomware incidents: Require the reporting of ransomware attacks to law enforcement, ensuring these incidents are brought to light. This will enhance intelligence-sharing, enable timely warnings about emerging threats, and focus law enforcement efforts on disrupting the most harmful ransomware groups.
The measures align with the government’s broader efforts to bolster the UK’s cyber defences and safeguard critical infrastructure and essential services. They build on recent successes like Operation Cronos, a global NCA-led effort that disrupted the LockBit cybercrime network.
They also support the UK-led Counter Ransomware Initiative (CRI), which published global ransomware resilience guidance in September 2024 with backing from 40 member nations and eight major insurance bodies. In October 2024, joint UK, US, and Australian actions sanctioned 16 individuals tied to the Evil Corp and LockBit cyber gangs.
How many ransomware attacks are there in the UK?
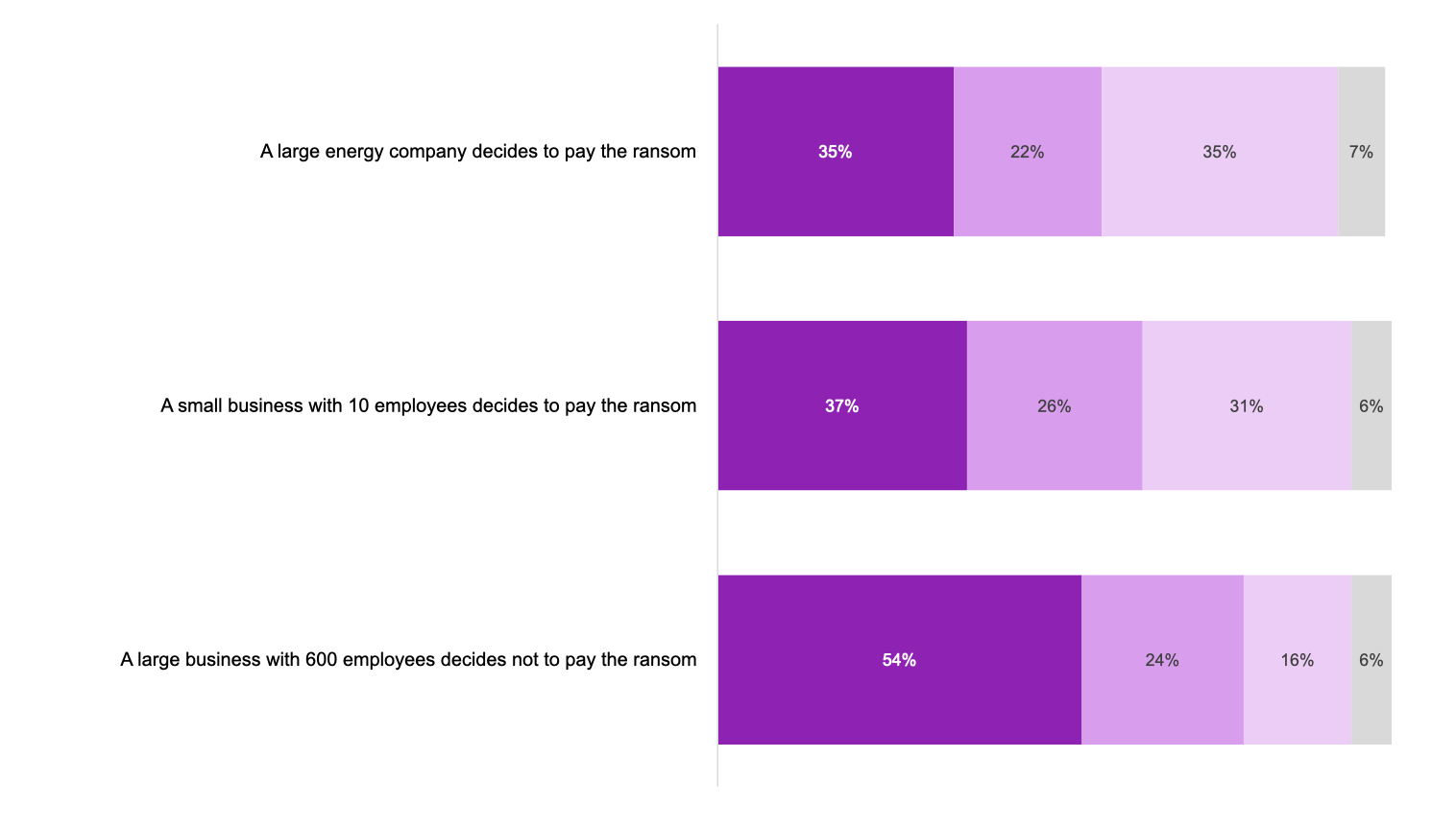
The NCSC managed 430 cyber incidents between September 2023 and August 2024, including 13 ransomware incidents deemed nationally significant and posing serious harm to essential services or the wider economy. The NCA said the number of UK victims appearing on ransomware data leak sites has also doubled since 2022.
Additionally, the Crime Survey for England and Wales also estimated that almost a million (952,000) computer misuse offences were committed against individuals in England and Wales in the year ending June 2024.
Richard Horne, National Cyber Security Centre CEO, said resiliency was key to combatting ransomware.
“Organisations across the country need to strengthen their ability to continue operations in the face of the disruption caused by successful ransomware attacks," he said. "This isn’t just about having backups in place: organisations need to make sure they have tested plans to continue their operations in the extended absence of IT should an attack be successful, and have a tested plan to rebuild their systems from backups."
Don't let crime pay: How to deter ransomware attacks

Christian Borst, EMEA CTO at Vectra AI, said organisations need to eliminate security blind spots to meet the proposed requirements, as cybercriminals are increasingly using multi-surface attacks to infect victims with ransomware.
“If the UK government proceeds with its proposed recommendations, public sector bodies and Critical National Infrastructure (CNI) firms aren’t relieved from reviewing their cybersecurity posture against ransomware. This is particularly important for healthcare firms, where attacks have risen by 179% according to the ICO.
“Affected UK organisations will need to arm themselves with the ability to spot cyber attacks including ransomware at the earliest possible stage, and make sure they can share information and report the incident to the authorities in good time. If not, they could fall foul of future regulations, and face significant reputational and financial damage.
“However, at the same time, threat actors are increasingly targeting weak spots in public sector and CNI organisations – exploiting security gaps in identity systems, public cloud, SaaS and data center networks to carry out hybrid attacks and infect victims.
"In response, enterprises need to eliminate security blind spots and understand their exposure to multi-surface attacks. This means improving extended detection and response capabilities and using AI to boost cyber capabilities and increase understanding their exposure to attacks – including third-party services and suppliers.”
What could happen when ransomware payments are banned?
Criminals don't just give up and go away. They start thinking of new ways to target victims.
Mike Kiser, Director of Strategy and Standards at SailPoint, predicted the rise of a new dark market built by providers of services that facilitate the covert exchange of ransom payments. Organisations that are desperate to restore operations might resort to breaking the law to save themselves.
A ban could also obscure the true scale of ransomware activity, making it harder for law enforcement agencies to track and combat cybercriminals.
Additionally, the question of accountability becomes murky in such a scenario. If an organisation covertly pays a ransom through underground channels, it's far from clear who is responsible for the offence: the corporate entity as a whole or the individual security executives who make the decision under pressure.
“Ransom payments should be banned: increasing payouts mean a corresponding rise in malicious activity," Kiser said. "However, as soon as laws are passed to ban ransom payments, an underground market is likely to arrive – resulting in a hidden economic system.
"Who is then held responsible for violating laws - is it the corporate entity or the fault of the security executive? The time for action to mitigate the rise of ransomware is now. But as with so many other elements of life, prevention is better than cure.”
Have you got a story or insights to share? Get in touch and let us know.




