The DORA explorer: A Compliance Day guide to new EU regulations
Machine speaks to experts and insiders to discuss how to respond to European rules governing the cybersecurity of financial entities.

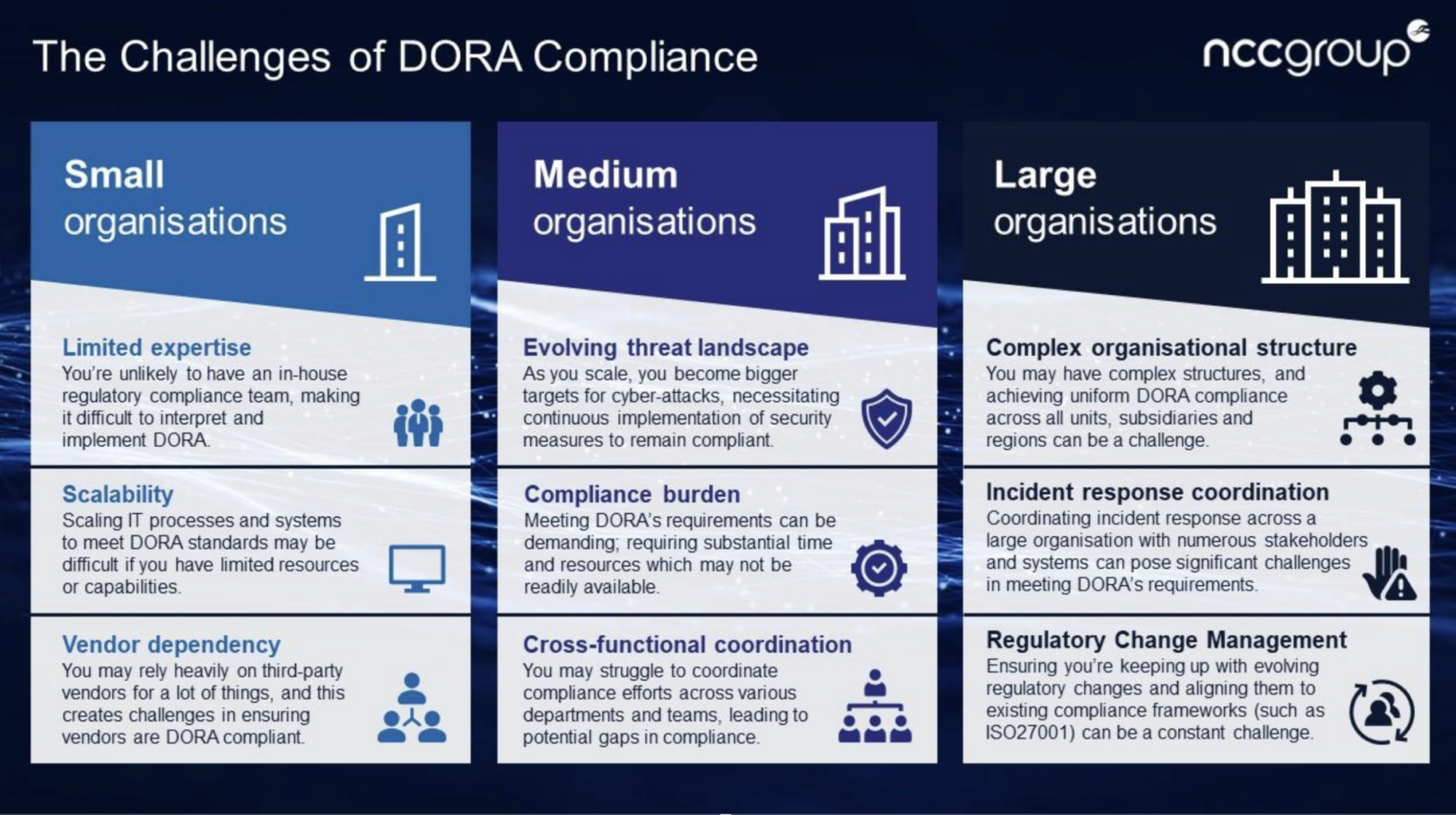
Today is the compliance deadline for the EU's Digital Operational Resilience Act (DORA), a regulation designed to improve the IT security of financial institutions and backed up by the threat of gigantic fines.
The vast amounts of lucrative data held by entities like banks, insurance companies and investment firms make them an obvious target for cybercriminals.
DORA aims to harden the cybersecurity of all players in the European financial sector and allow them to stay standing during severe operational disruption.
Penalties for noncompliance are severe, especially for businesses considered critical third parties (CTPs), such as cloud platforms, software vendors, and data analytics firms, whose failure could cause cascading disruption throughout the financial system on the continent and across the world. Here's a Deloitte guide to understanding how the EU and UK define a CTP.
Fines stretch up to 2% of a firm's total annual worldwide turnover, whereas for individuals, fines can reach €1,000,000. For critical third-party providers, penalties can be as much as €5,000,000. The exact amount will vary depending on the severity of the violation and the entity's cooperation with authorities.
Mike Arrowsmith, Chief Trust Officer at NinjaOne, told Machine: “DORA is an essential response to the relentless escalation of cybersecurity threats to the financial services industry.
“While implementation focuses on EU members, it also has a direct impact on the UK. Not only will the financial entities operating in the EU need to be compliant, but ‘critical’ providers will also be regulated by the EU authorities.
"DORA represents a significant challenge for the industry. Outdated systems may not only fail to meet DORA’s standards but are also vulnerable to attack, putting financial institutions and their customers at risk."
Arrowsmith said that automated endpoint management was one way of addressing risk and ensuring compliance.
But what else can businesses do to protect themselves from the EU's hyper-zealous regulators? Machine spoke to tech industry leaders to find out.
You have zero seconds to comply...

Jason Smith, Senior Principal, Strategy & Transformation at Conga said organisations have scrambled to ensure that their systems, governance structures and reporting processes meet the new standards, with financial institutions accelerating investments in cybersecurity infrastructure, conducting rigorous testing of their IT frameworks, and enhancing third-party risk management practices.
The "more effective" firms may have implemented a centralised contract lifecycle management (CLM) system to automate vendor risk assessments and ensure contractual agreements meet the new standards.
"However, firms without the technological infrastructure in place may still have gaps in their third-party risk oversight," Smith warned. "As the transition period draws to a close, organisations must remain vigilant. Whilst the main concern is whether financial institutions and their partners are fully compliant, DORA is not a one-time effort; firms must continuously refine their resilience strategies and stay prepared for potential regulatory updates.
"Organisations should remain proactive, ensuring they meet the current requirements but are also in the best position to adapt to future legislation. The post-DORA landscape highlights a clear lesson: operational resilience is now a strategic imperative.”
The best of times for EU regulators, but the worst of times for everyone else?
Eurocrats have been on a regulatory spree for many years now. In addition to DORA, the Network and Information Systems Directive 2 (NIS2) Directive to enhance security in 18 critical sectors was transposed into national law in October 2024. The PSD3/PSR1 are also in the pipeline. These rules follow up on the PSD2, the directive that created open banking in Europe, and will modernise EU payment services on an unclear implementation timeline.
Richard Lindsay, Principal Advisory Consultant at Orange Cyberdefense, said: “Frankly, the regulatory landscape in the EU is heavily congested right now, with several overlapping standards and laws, with more in the pipeline.
"Remember, only three months ago, another significant EU regulation, NIS2, took effect. This persistent need to address broader compliance demands with similar requirements might explain why nine in ten UK financial services CISOs felt optimistic about their organisation’s preparedness ahead of the DORA deadline. In reality, however, a little less than half (43%) of respondents will miss that deadline, with 20% expecting to do so by at least three months, according to our latest survey.
“Remaining non-compliant is likely to have severe ramifications. Firstly, the financial services industry is an attractive target for bad actors, and the likelihood of breach has never been higher. Secondly, DORA is not toothless – fines of up to 1% of worldwide daily turnover and over €1m for individual senior leadership are significant and can certainly be used by IT and security leaders to reiterate the importance of cybersecurity and compliance to the board.
“All in all, DORA doesn’t mandate anything by way of revolutionary requirements. Most can be addressed by investing in comprehensive cyber risk assessments, integrated incident reporting, cyber resilience testing and cross-framework governance. However, amid the tangle of new regulations, it’s understandable that many firms are taking a more reactive approach to compliance requirements once the threat of reprisals becomes tangible.”
Beyond regulation: Going the extra mile to comply with DORA
Bob Wambach, VP of Product Portfolio at Dynatrace, advised that compliance will "only take banks so far".
"Financial services firms both in Europe and the UK must be prepared not just to meet the baseline requirements of DORA, but to empower their teams to respond instantly to operational disruption and cyber incidents," he continued. "This means going beyond checkbox compliance measures. Organizations must prioritise continuous testing of their services and embrace a culture of resiliency first.
"Converging observability and security data to support real-time, AI-powered anomaly detection is the optimal way to rapidly assess risks before they escalate into full-blown incidents that breach compliance thresholds and leave customers exposed.
“It remains to be seen how strictly EU regulators will enforce the rules surrounding DORA, but one thing is certain: no financial institution wants to be the first to fall short.”
Ev Kontsevoy, CEO of Teleport, said the journey to achieving DORA compliance "will surely be long and challenging for the financial services sector".
For instance, the first pillar of DORA around Information and Communication Technology (ICT) risk management requires financial institutions to rework their risk management from reactive to proactive.
“Unfortunately, many financial institutions still struggle to gain visibility into their IT and infrastructure environments," Lindsay continued. "The consequences for lagging behind on infrastructure access security are substantial."
He advised banks to gain visibility into infrastructure assets and associated access permissions to enforce ICT risk management policies and conduct ongoing risk assessments.
"In financial services, we’re talking about a significant volume of access relationships, spread across disparate systems," Lindsay warned. "Without a centralised platform, organizations are unable to audit who has access to what. Enforcing policies that support compliance regulations becomes impossible.
Transforming access and security models will also help financial services organizations reduce their attack surface and streamline compliance. Just-in-time access, for instance, delivers visibility of the minimum access needed for a user to do their job.
Lindsay added: "Moving from standing privileges towards ephemeral, task-based access, coupled with secretless authentication, will enable financial institutions to reduce the risk of unauthorized access - a key principle of DORA. This approach eliminates the potential for credential misuse and provides the visibility that organizations need to achieve compliance."
Reassuring words for the financial services sector

Andre Troskie, EMEA Field CISO, Veeam , said that the regulations might be tough - but the heavily regulated sectors they most affect are well-used to sturdy compliance burdens.
“Unlike other sectors, the financial service industry is no stranger to stringent regulation," Troskie said. "These organisations have worked hard on their data resilience and cybersecurity strategies. So while they have an additional regulation to comply with in DORA, the gap between where they are now and where they need to be should be manageable, at least with their internal operations.
However, it's "a whole other ball game" when it comes to third-party service providers and the wider supply chain, Troskie advised. This means focusing on securing the entire supply chain should be a priority.
"It doesn’t matter how ahead of the game you are internally. If you can’t guarantee the compliance of your relevant partners, you’ll struggle with demonstrating compliance, resulting in potential fines or other negative repercussions.
“At a minimum, organisations need to ensure that third parties implement robust risk management processes. As part of this, organisations need to require the renegotiation of all third-party service level agreements (SLAs) to cement DORA compliance as an essential prerequisite for work. Although time-consuming, organisations can’t afford to underestimate the importance of securing third-party compliance.”
A spotlight on CISOs

The dawn of DORA will place new levels of scrutiny on security leaders. Lauren Walters (pictured in this article' main image), a security evangelist with Panaseer, said: “With boards directly accountable for any failures to comply, CISOs can expect more questions over compliance, posture and risk. This mean security leaders can’t assume they know what assets they have in place.
"They need a reliable, centralised inventory that provides actionable insights – a golden source of truth data that includes all assets, controls, owners, criticality, and business context. This is crucial for identifying vulnerabilities, prioritising fixes, and demonstrating a clear understanding of risk and resilience to both the board and regulators.”
Chris Royles, EMEA CTO at Cloudera, told us that a unified hybrid data platform with the capability to seamlessly move data and applications between public cloud and on-premise is "essential" for DORA compliance.
"To stay ahead and compliant, a unified hybrid data platform is essential," he advised. "Having the capability to seamlessly move data and applications between public cloud and on-premise is central to this approach. Data security and governance can also be built in, with data applications operating the same everywhere.
"This portability helps address DORA’s concerns around cloud vendor lock-in, cloud consolidation risks while also enhancing digital operational resilience for financial institutions.”
Mo Joueid, an identity security consultant at SailPoint, advised firms to evaluate the entitlements of each entity operating within their systems, ensuring access is granted on a "need-to-know basis" only.
“As DORA comes into effect, firms must evaluate the entitlements of each entity operating within their systems, ensuring access is granted on
a need-to-know basis only," Joueid said. "This includes processes that carefully manage the onboarding and offboarding of non-employees, as well as the lifecycle in between.”
Contact Jasper@machine.news to let us know how you're getting on with DORA
Have you got a story or insights to share? Get in touch and let us know.




