The big threat facing small businesses: How SMEs should respond to a growing cybersecurity risk
"Profit-hungry cyber gangs know they can easily hit a dozen vulnerable operations for the effort of a single larger strike."

Big cyberattacks tend to dominate the headlines. Threats to critical national infrastructure. Multinational companies hit with multi-million-dollar ransom demands or shoppers facing identity theft after their personal details were flogged on the black market.
But behind the scenes, small and mid-sized enterprises (SMEs), schools, and nonprofits are also battling cybercrime, facing down adversaries seeking to exploit their resource-constrained difficulty in detecting and halting attacks.
In an interview with Machine, Mike Britton, CIO at Abnormal Security, discusses the growing scale of the threat to SMEs and other organisations with limited budgets and how they can best defend themselves.
Is email still a primary attack vector?
"Absolutely. Despite the rise of collaboration apps like Zoom, Teams, and Slack, email is still the most popular communications tool for most businesses. And because people inherently trust their email platforms, it’s one of the most obvious channels for cybercriminals to target their victims – especially through social engineering attacks.
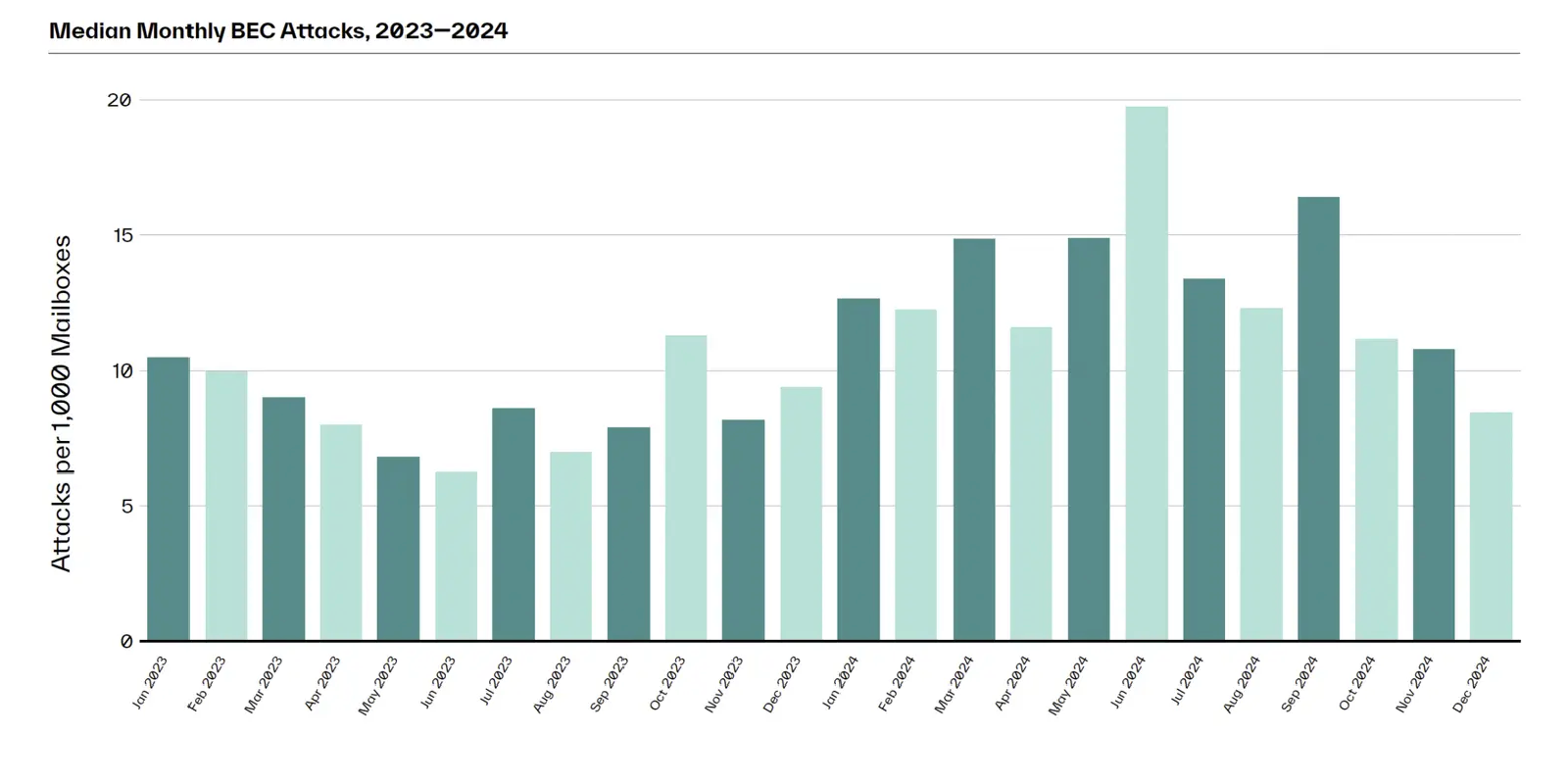
"Our research found that phishing emails are by far the most common threat vector, accounting for 76% of all advanced cyberattacks. We’ve also seen a sharp increase in the more advanced Business Email Compromise (BEC) approach, with more targeted text-based attacks mimicking colleagues and other trusted contacts. BEC attacks have surged 54% year-over-year, with an estimated cost to businesses of $2.9 billion in 2023 alone."
Why are so many of these attacks aimed at smaller targets?
"SMEs are definitely bearing the brunt of this rise in email attacks. We found that organisations with 1,000 inboxes or fewer face a 70% weekly chance of suffering a BEC attack, a 14% rise from last year. As well as the size of the operation, it’s also down to the available budget for IT security.
"Unlike large corporations with dedicated security teams and vast budgets, these companies typically lack full-time security staff. If mega corps armed with advanced tools and elite SOC teams still face regular breaches through malicious emails, what chance does a school with one IT guy on call stand?
"Profit-hungry cyber gangs know they can easily hit a dozen vulnerable operations for the effort of a single larger strike, scooping up guaranteed loot in the form of stolen data and ransom demands.
"Further, while large businesses are likely to have contingency plans, insurance support, and the sheer scale to weather an incident, many less well-financed operations face ruin from a single attack - especially when the victims are public services like schools."
Just how bad is the email risk for smaller organisations?
"It’s one thing to see the email attack statistics ticking up year-on-year, but you really get a sense for the situation when you talk to the organisations being targeted.
"One good example is Saskatoon Public Schools in Saskatchewan, Canada. It’s a school division serving more than 25,000 students across 60 schools. There are a lot of kids relying on it for their education, but by business standards it’s pretty small – less than 5,000 inboxes and only enough budget for a limited IT team.
"In other words, it’s a perfect target for criminal groups looking for organisations where minimal effort can have maximum impact.
READ MORE: The UK's supply chain is heavily reliant on "Chinese military companies", Bitsight warns
"Within six months of working with them, we’d already detected and stopped over 25,000 attacks, of which at least 160 were targeted account takeover attempts. In one case, an attacker had compromised an employee’s account and used it to quickly try to fire off 500 credential phishing emails aimed at internal inboxes.
"Luckily, we could detect and disable the account and remove the malicious emails before they could be opened. But these kinds of incidents happen all the time without any intervention to protect the victims.
"BEC attacks like this are particularly bad for schools, SMEs, and others with limited budgets because a single compromised account can cause some serious damage. Criminals impersonating CEOs, financial staff, IT heads can trick their victims into sharing all manner of private data and system access, as well as racking up huge losses in fraudulent payments."
Why are email security measures failing?
"The big problem is that many companies are still relying on basic email security solutions like Secure Email Gateways (SEGs) and spam filters that are typically built to look for known threat signatures.
"This is still effective for stopping the kinds of low-effort, high-volume attacks that are still being sent out in huge numbers. But it really falls short when it comes to detecting more subtle phishing and impersonation tactics. Relying on predefined rules rather than using behavioural analytics leaves a blind spot for new techniques designed to bypass existing filters.
"Traditional solutions also tend to be very heavy on manual intervention, requiring IT and security staff to pour hours into remediation or adjusting settings. In the email compromise case with Saskatoon Public Schools for example, the systems programmer knew it would have taken him many hours to sort out those 500 rogue emails.
"Without effective email defences reliably stopping malicious messages from reaching target inboxes, staff must be able to stop scams. But widespread, in-depth anti-phishing programmes aren’t really feasible for many companies either, especially in public fields like education, where budgets are already stretched thin."
So, are these companies doomed to suffer email attacks? What can they do to fight back?
"Unfortunately, I think we’re likely to see the number of attacks targeting SMEs and other vulnerable operations continue to climb. Breaching a big multinational is like a lottery win compared to the reliable 9-to-5 paycheque of going after smaller operations. Cybercriminal groups will always be drawn to a perceived easy win.
"But that doesn’t mean things are hopeless for those with limited resources. Even without the budget of big enterprises, it’s still possible for them to keep up and protect their inboxes from constant attacks.
"Automation is probably the most important capability here. With so many malicious emails coming in, dealing with them manually is like trying to empty the ocean with a bucket - even the largest IT security teams wouldn’t have a prayer of keeping up.
"The good news is that an efficient, automated email defence is still within the reach of SMEs that lack big budgets, as a few key tools can do most of the heavy lifting.
"This is where AI-powered tools really shine. AI excels at dealing with large volumes of data, identifying patterns, and spotting anomalies, which makes it ideal for detecting impersonation attempts. AI analytics tools can learn a business’s baseline for normal communication so that anything outside the norm immediately throws up red flags.
"Heavily automating email security also provides the 24/7 monitoring and rapid remediation smaller firms need to handle threats, without having to budget for a whole IT security team. While threat actors will continue to target smaller and more vulnerable operations, those with the ability to detect and block malicious emails quickly will have the best chance of fending off attacks."
Have you got a story or insights to share? Get in touch and let us know.