The art of cyber-war: Chinese threat actors escalate global operations
CrowdStrike issues red alert as China and "Four Eyes" nations intensify digital blitzkrieg against targets including the West.

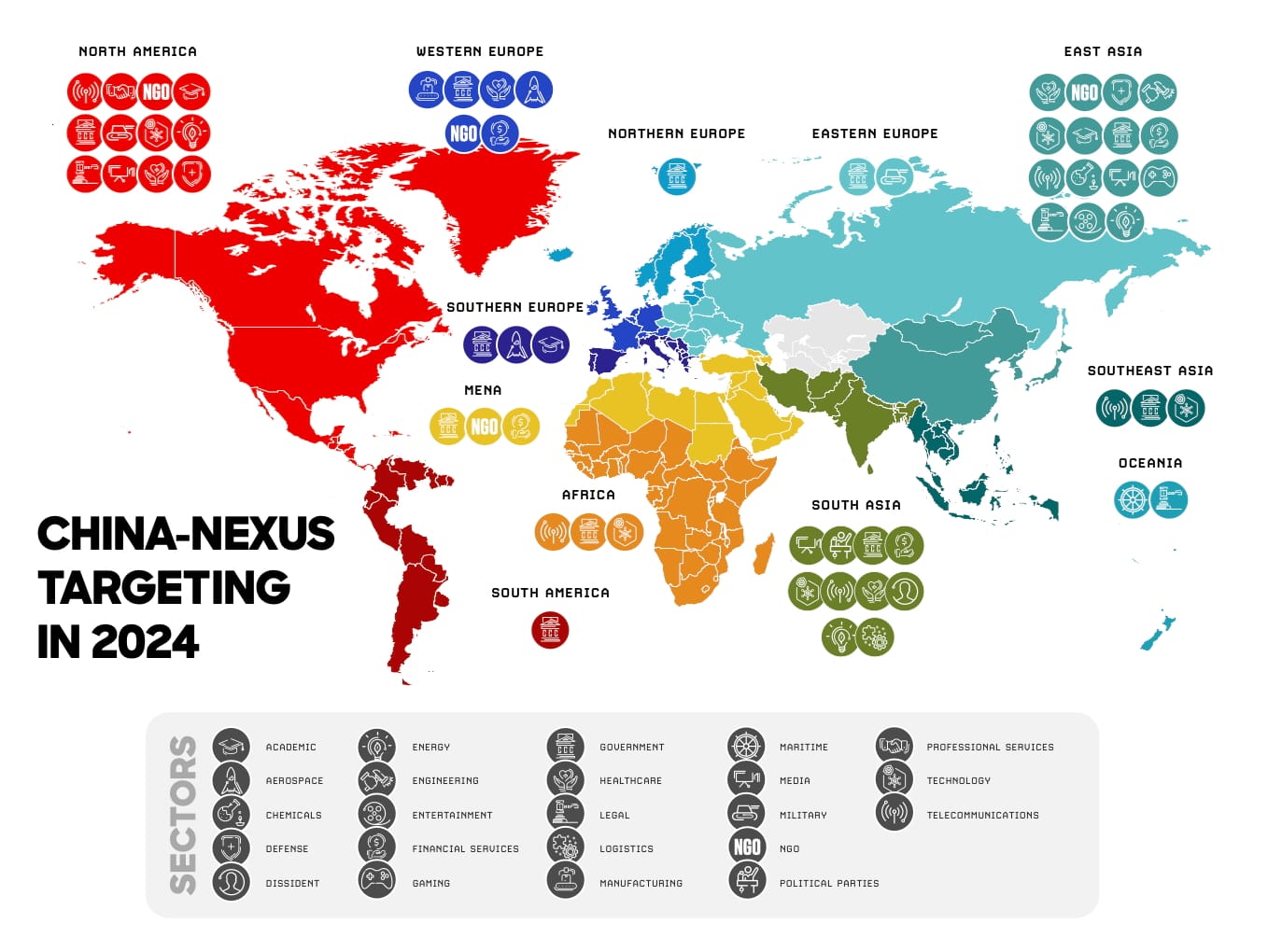
The activity of China-linked threat actors soared by an average of 150% in 2024 as Beijing's cyber-espionage operations reached "new levels" of maturity and sophistication.
In its latest Global Threat Report, CrowdStrike said that "China-nexus" adversaries stepped up their attacks on sensitive industries including media, manufacturing, heavy industry and financial services by up to 300%.
Attacks on the three most popular targets - technology, government and telecommunications - escalated by 50%.
CrowdStrike Intelligence identified seven new targeted intrusion adversaries originating from China in 2024. Five of these are "unique in their specialisation and sophistication".
Liminal Panda, Locksmith Panda and Operator Panda are "high-capability adversaries" focused on targeting telecom networks. Vault Panda is focused on finance, whilst Envoy Panda has gone from a "low capability" enemy to a more fearsome adversary with a significantly more advanced OPSEC posture.
"The emergence of adversaries with unique tactics, tradecraft, and target scopes represents an ongoing shift in China-nexus intrusions from so-called smash-and-grab operations to increasingly focused and mission-specific intrusions," CrowdStrike wrote.
China's digital partisans are motivated by the CCP's wider mission to make the nation a leading global power and carry out intelligence-gathering operations against foreign political and military entities. They also target social and political movements regarded as domestic security threats, including groups the CCP calls the "Five Poisons" (Falun Gong practitioners, Chinese democracy activists, and Uyghur, Tibetan, and Taiwanese separatists).
“China’s increasingly aggressive cyber espionage, combined with the rapid weaponization of AI-powered deception, is forcing organizations to rethink their approach to security,” said Adam Meyers, head of counter adversary operations at CrowdStrike.
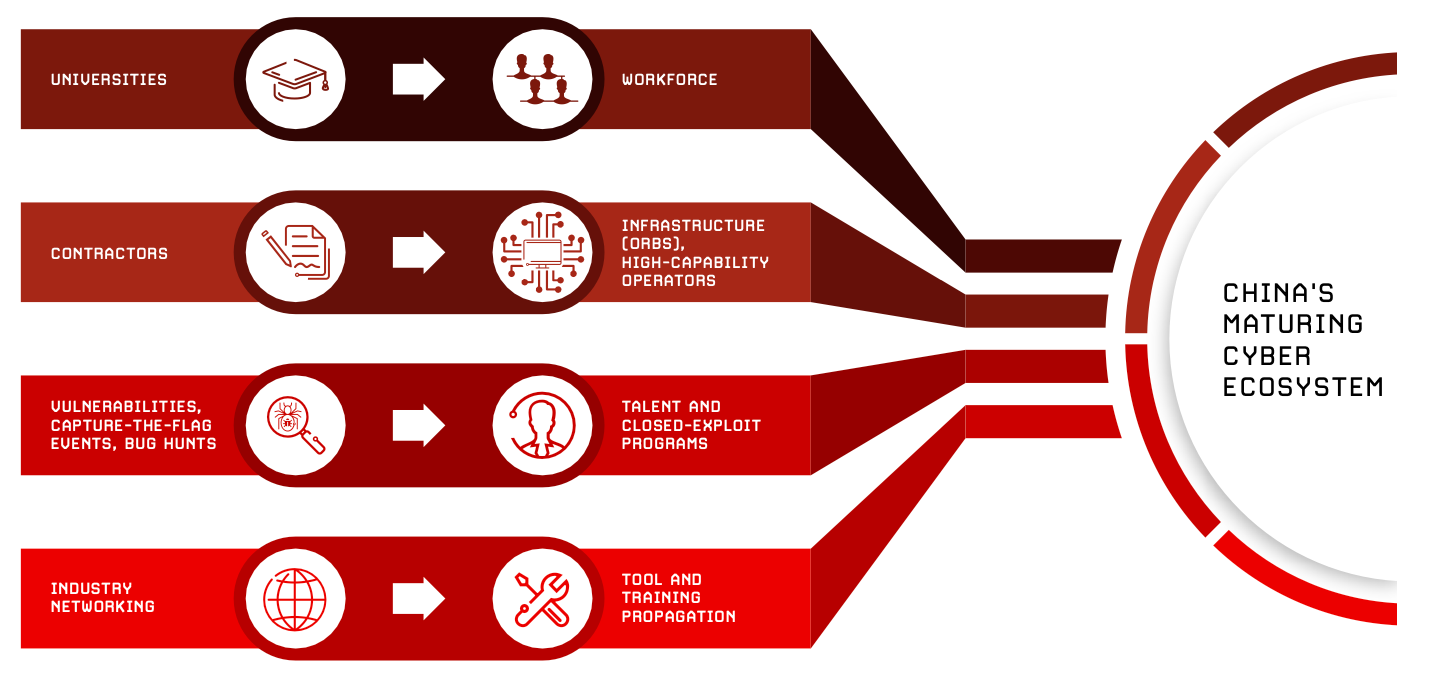
“Adversaries exploit identity gaps, leverage social engineering and move across domains undetected—rendering legacy defences ineffective. Stopping breaches requires a unified platform powered by real-time intelligence and threat hunting, correlating identity, cloud and endpoint activity to eliminate the blind spots where adversaries hide.”
Other nations from the emerging Four Eyes alliance also reared their heads throughout 2024. Both Russia and Iran-affiliated threat actors conducted AI-driven disinformation and influence operations to disrupt elections.
Iranian groups were observed increasing their use of GenAI for vulnerability research, exploit development and patching domestic networks, aligning with government-led AI initiatives.
Kim Jong-un's highly persuasive digital army
North Korea's Famous Chollima managed to install its operatives within companies around the world under fake personas, sometimes using GenAI to trick recruiters during the job application process. These fake employees would send their company's computers to laptop farms in Illinois, New York, Texas, and Florida.
Famous Chollima sometimes targeted companies to exfiltrate data or steal intellectual property. Sometimes, however, they appeared to be motivated simply by earning a semi-decent salary.
The group also created fake LinkedIn profiles, as well as using more typical techniques such as a trojanised Node.js application.
Faster, stronger and more deadly: The changing face of cybercrime

CrowdStrike warned that adversaries are now acting at "unprecedented" speed.
The breakout time - a measure of how long it takes for an attack to move laterally - reached an all-time low among criminal adversaries, plunging from 62 minutes in 2023 to just 48 in 2024. The fastest breakout CrowdStrike recorded was just 51 seconds.
A gang called Curly Spider emerged as one of the quickest and most effective adversaries.
It floods targets with spam, then follows up with a vishing call posing as IT support. Victims are tricked into granting remote access via tools like Quick Assist, allowing attackers to deploy malicious scripts within seconds.
By modifying registry keys and erasing traces, they embed persistence before the call ends. CrowdStrike OverWatch intercepted and blocked one such attack in under four minutes, stopping the adversary before lasting damage was done.
Adversaries worldwide are now weaponising AI-generated deception, exploiting stolen credentials and increasingly executing cross-domain attacks - exploiting gaps across endpoint, cloud and identity.
There has also been a shift to malware-free intrusions that exploit trusted access, indicating adversaries are using hands-on-keyboard techniques to blend in with legitimate user activity and make detection more difficult. 79% of detections in 2024 were malware-free, up from 40% in 2019.
Is vishing the new phishing?
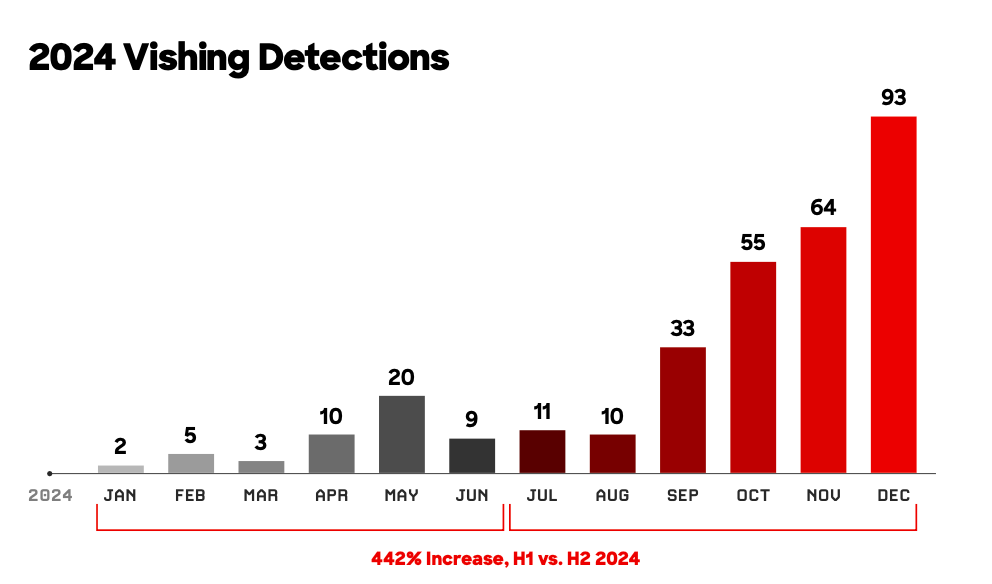
Digital crooks have started moving away from phishing in favour of alternative access methods, suggesting that malware operators are seeking more effective and innovative techniques as they face hardened defences.
Voice phishing (vishing) attacks, involving calls to victims and persuasive social engineering techniques, saw an "explosive" rise in popularity - soaring by 442% between the first and second half of 2024.
"To stop modern attacks, security teams need to eliminate visibility gaps, detect adversary movement in real-time and stop attacks before they escalate - because once they’re inside, it’s already too late," CrowdStrike advised.
Have you got a story or insights to share? Get in touch and let us know.




