Russian cyber-warriors blitz Europe in bid to "disrupt societal stability"
Kremlin-linked actors wage war on democratic institutions and seek to undermine trust in Western nations.

Europe has become the main target of a prominent Russian state-linked group of "cyber-warriors" as they seek to erode democracy and undermine citizens' trust in Western states.
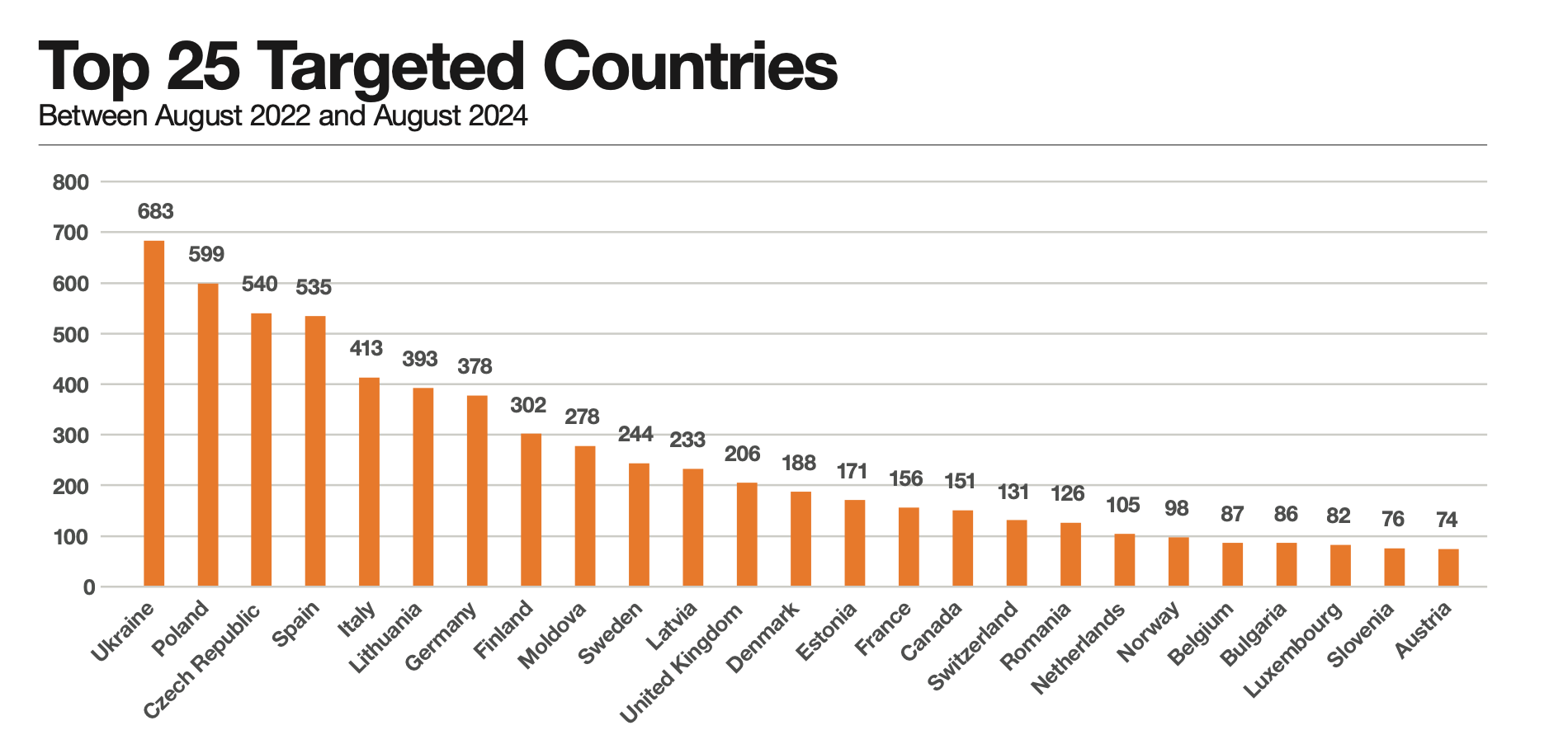
Investigators from Orange Cyberdefense spent two years monitoring a prominent Russian hacktivist group and found that 98% of their operations targeted Europe.
Rather than seeking to cause digital or physical damage, the hackers sought to "disrupt societal stability".
"By targeting symbolic infrastructure and leveraging public platforms like Telegram, these groups blur the line between cybercrime and influence operations," Orange Cyberdefense wrote in its Security Navigator 2025 report. "Their ultimate objective isn’t solely system disruption, but rather the erosion of trust in democratic systems and processes."
Pro-Russian hacktivist groups typically launch campaigns focused around major geopolitical events, including elections or summits, to "amplify their impact".
They "align with state-sponsored agendas", targeting critical infrastructure such as electoral systems and other "symbolic institutions" in a bid to "undermine public trust, disrupt the flow of information, and potentially influence the outcome of a key democratic process".
Exposing Kremlin-linked hacktivists
The group leverages sophisticated DDoS-for-hire services and anonymous cryptocurrency ransom techniques, public shaming and extortion to "exploit fear and amplify public pressure".
"While Europe is the primary focus for the group, everyone is a potential target, and the problem threatens societies as a whole," Orange Cyberdefense wrote.
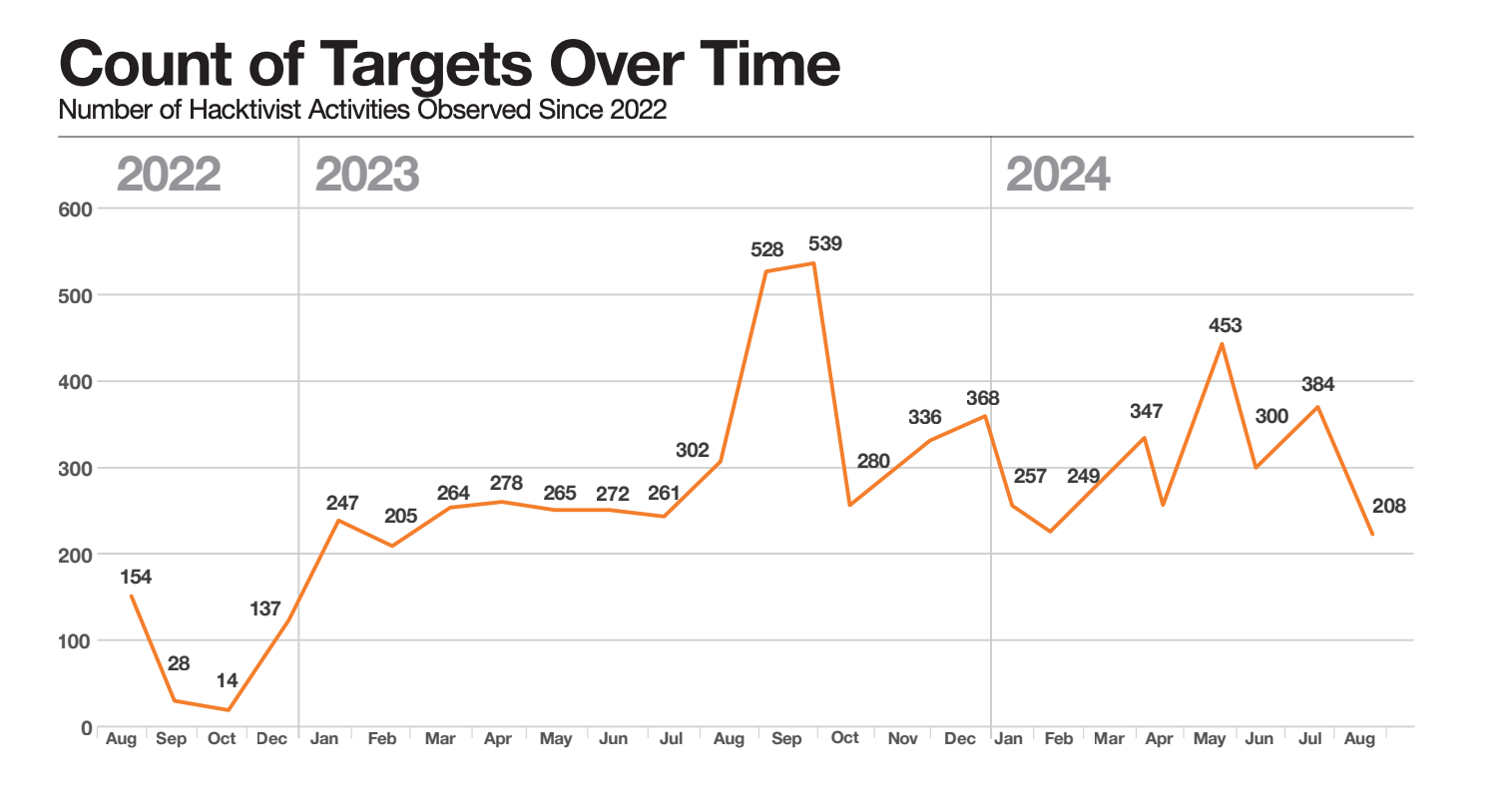
The pro-Russian hacktivist group has been active for 2.5 years and began operations after Putin launched his war against Ukraine. Between August 2022 and August 2024, it claimed to have carried out 6,600 attacks.
Hugues Foulon, CEO of Orange Cyberdefense, stated: “Cyber threats have become a critical barometer for anticipating global geopolitical tensions."
Diana Selck-Paulsson, Lead Security Researcher, and Ben Gibney, Security Analyst, scraped 3,200 messages from the group's Telegram page to find that 96% of victims were in Europe - a finding that aligned with its clearly stated "anti-NATO and anti-Western stance".
"Surprisingly, despite frequent mentions, no attacks were observed on U.S. targets, possibly signalling an intentional avoidance," the researchers wrote.
The group focuses on essential sectors such as transport, education, government systems and financial services.
President Putin's digital paramilitary
Voting systems in France, the UK, Finland, Belgium and Austria were all targeted during elections, "threatening electoral integrity and sowing doubt about results".
"These attacks align closely with Russian state narratives, suggesting potential state influence," Orange wrote.
"Election interference represents an escalation beyond typical DDoS attacks on infrastructure or military websites, as it directly targets the democratic process of a nation. By attacking election-related websites and portals, the hacktivist group aims to undermine public trust in the electoral system, disrupt the flow of information, and potentially influence the outcome of a key democratic process."
The group often frames its actions as "retaliation" for Russophobia, Western support for Ukraine, or sanctions on Russia, the researchers found.
They added: "Messages often mock targeted nations, criticizing leaders for prioritizing Ukraine over domestic issues. They use militaristic language, praising Russia’s military and positioning themselves as cyber warriors defending Russia's interests, and aligning with broader narratives of resisting Western influence."
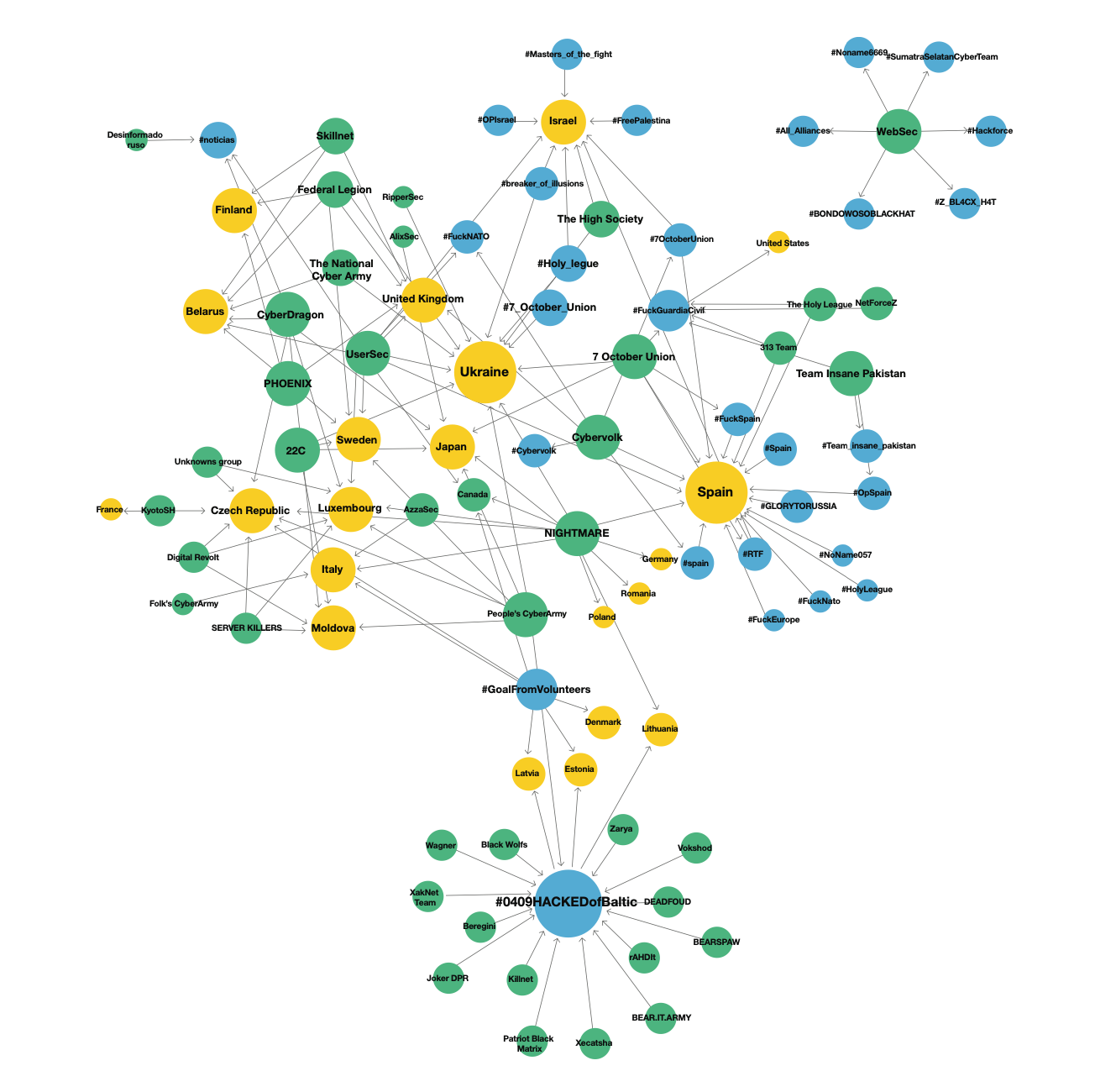
The Russian cyber-warriors also mentioned 48 other causes in the messages, ranging from the #FreePalestine movement to the #FuckGuardiaCivil campaign in Spain that erupted after the arrests of three individuals linked to a separate group. You can see some of these links in the graphic below.
Attacks on operational technology (OT)
Another major concern raised in the report is hacktivist activity targeting OT systems in critical national infrastructure including the manufacturing, energy, healthcare and transportation sectors. Investigators attributed nearly 1 in 4 (23%) of sophisticated attacks on OT to hacktivists.
These attackers have typically been associated with state actors, indicating that hacktivists are becoming more skilled and ambitious, posing a risk to critical infrastructure.
Roughly half (46%) of OT cyber-attacks resulted in "manipulation of control" in which adversaries manipulated physical processes. The utilities sector suffered 46% of attacks that directly targeted OT systems.
Hugues Foulon added: "Our research underscores an urgent need for coordinated defensive strategies across Europe and beyond, including enhanced incident response measures, strengthened OT protections, and proactive monitoring of public channels to counter the unique blend of cyber extortion, hacktivism, and cognitive warfare facing European organizations."
Have you got a story to share (or are you a hacktivist wanting to share your side of the story in confidence and with the understanding that we will be 100% neutral)? Get in touch and let us know.




