Kim Jong-unemployable: Exposing fake North Korean tech workers
"The staggering volume of ongoing infiltration attempts far outpaces any other insider threat vector we monitor," SentinelOne warns.

Vast numbers of North Korean spies have managed to trick Western companies into giving them jobs, creating an insider risk of an almost unparalleled scale.
Now cyber security firm SentinelOne has revealed details of its own battle against Kim Jong-un's army of fake workers, as well as details of how to mitigate this growing threat.
It said there has been an explosion in the number of phoney employees who take remote jobs whilst secretly working for the Democratic People's Republic of Korea (DPRK).
Although this scam has been widely reported, it is unusual for a company to be so frank about its own battles with the hordes of Kim Jong-unempoyables.
"One of the more prolific and persistent adversary campaigns we’ve tracked in recent years involves widespread campaigns by DPRK-affiliated IT Workers attempting to secure remote employment within Western tech companies– including SentinelOne," it wrote in a report published today.
"Early reports drew attention to these efforts, and our own analysis revealed further logistical infrastructure to launder illicit funds via Chinese intermediary organisations.
"However, neither gave a sense of the staggering volume of ongoing infiltration attempts. This vector far outpaces any other insider threat vector we monitor."
The genuine threat from fake DPRK workers
Pyonggang's threat actors actually sound like they would make great employees, working hard to refine their processes, leveraging stolen personas and adapting outreach tactics to make their scams ever more convincing.
However, once inside companies they have been known to steal intellectual property, gather sensitive data, install information-stealing malware, extort cash to pay for ballistic missile programs or encrypt data and then issue ransom demands.
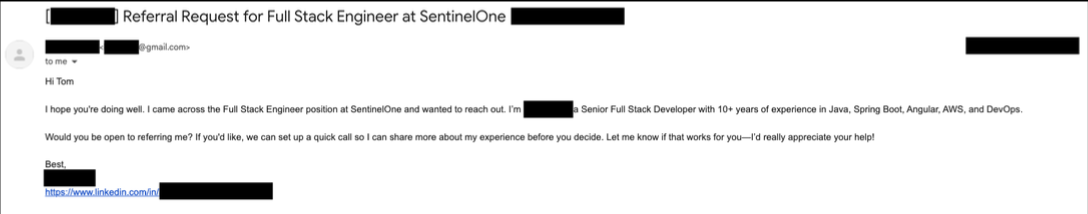
SentinelOne alone has tracked roughly 360 fake personas and over 1,000 job applications linked to DPRK IT worker operations - including "brazen" attempts to secure positions on its intelligence engineering team.
It warned that spies' "craftiness and persistence" are making them increasingly difficult to identify.
"The attackers are honing their craft beyond the job application and recruitment process," SentinelOne reported.
"An operation of this scale and nature requires a different kind of backend infrastructure, such as a sprawling network of front companies to enable further laundering and logistics."
To help recruiters spot the dupes, SentinelOne shared "threat context" with recruitment teams.
"Rather than cluelessness, we encountered an intuitive understanding of the situation as recruiters had already been filtering out and reporting ‘fake applicants’ within their own processes," it said.
"We brought campaign-level understanding that was combined with tactical insights from our talent team. The payoff was immediate. Recruiters began spotting patterns on their own, driving an increase in early-stage escalation of suspicious profiles.
"They became an active partner that continues to flag new sightings from the frontlines. In turn, we are codifying these insights into automated systems that flag, filter, enrich, and proactively block these campaigns to lower the burden on our recruiters and hiring managers, and reduce the risk of infiltration."
North Korea advice: How to deal with the DPRK's dodgy job applicants
SentinelOne called on leaders to:
- Make cross‑functional collaboration a standard operating procedure.
- Equip frontline business units from recruiting to sales with shared threat context and clear escalation paths to surface anomalies.
- Codify insights with automation to "consistently bring bi-directional benefits".
- Share intelligence throughout the organisation.
SentinelOne added: "The DPRK IT worker threat is a uniquely complex challenge - one where meaningful progress depends on collaboration between the security research community and public sector partners.
"As criminal groups increasingly impersonate legitimate businesses to acquire security products through trusted resellers, intelligence plays a key role in verifying customer legitimacy and identifying anomalous purchase behaviours. By integrating intelligence insights into pre-sale vetting workflows, a crucial layer of protection is helping to ensure adversaries cannot simply 'buy' their way into our technology stack."
SentinelOne is one of many companies that have faced infiltration from Pyongyang's armies of fake workers.
Adam Meyers, Head of Counter Adversary Operations, CrowdStrike, told Machine: “In 2024, CrowdStrike observed that FAMOUS CHOLLIMA — a North Korea-linked adversary — was behind over 300 incidents, nearly 40% involving insider threats. CrowdStrike’s counter-adversary operations team has seen the adversary exploit remote hiring at scale, using fake identities and AI-generated resumes to land IT jobs and redirect company-issued laptops to 'laptop farms.'
"To defend against this insider threat, hiring teams must treat recruitment as a security-critical process: verify identities rigorously, use live video onboarding and work hand-in-hand with IT, legal and security. Post-hire, watch for behavioural red flags like unusual login patterns or chronic underperformance — and ensure threat intel and proactive threat hunting are part of your ongoing defence.”
Do you have a story or insights to share? Get in touch and let us know.




