Inside the shadowy world of dark web Initial Access Brokers
It's boom time for threat actors who sell access to compromised networks and organisations, Check Point researchers warn

Initial Access Brokers (IABs) are making vast amounts of money in a dark web bull market that is growing at a frightening rate.
These cybercriminals break into organisations and sell access on underground forums, with customers including ransomware groups, nation-state actors, and other shady characters.
Now researchers from Check Point External Risk Management (formerly Cyberint) have shone a light into the shadowy world of IABs, describing these dark web dealers as managers of "the supply chain behind ransomware."
Investigators discovered that there has been a 90% increase in IAB listings across the top 10 most-targeted countries in 2024.
Selling access is profitable, scalable and relatively low risk, enabling IABs to "carve out a niche as critical suppliers in the global threat ecosystem, fuelling everything from ransomware-as-a-service (RaaS) to espionage", Check Point warned.
Which nations and industries are IABs targeting?
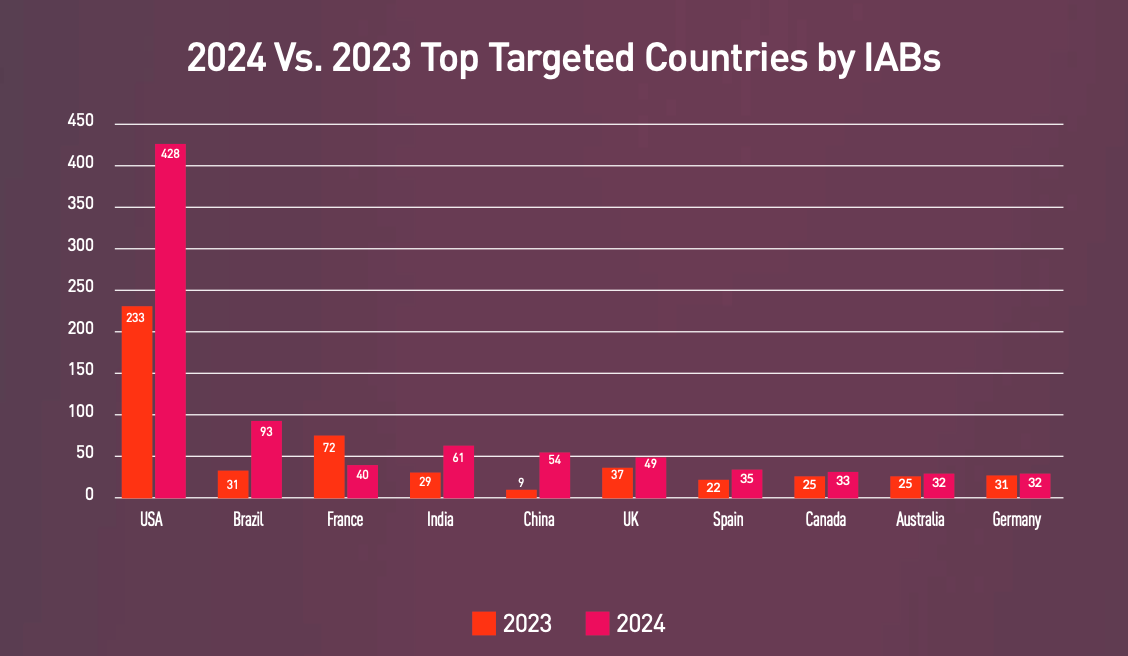
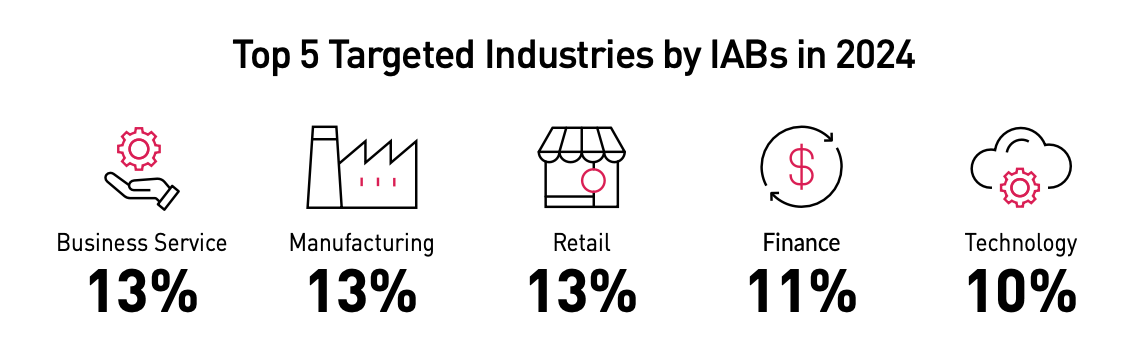
The US is the top target for IABs, who are becoming "more selective, strategic, and dangerous". It now accounts for 31% of listing on hidden markets. France and Brazil are growing targets, whilst there has also been an increase in activity aimed at the UK.
“Initial Access Brokers are the venture capitalists of ransomware. They invest effort in breaches and profit by selling access, empowering the entire cybercrime supply chain,” said Adi Bleih, Security Researcher, Check Point External Risk Management.
“Organisations must shift from reactive to proactive security: patch aggressively, segment networks, and monitor deep and dark web chatter to disrupt access before it’s sold.”
The Initial Access Broker Report drawers on dark web research carried out over the past two years.
It found that the new "sweet spot" for attackers is SMEs, with 60.5% of listings targeting companies with between $5 million and $50 million in revenue.
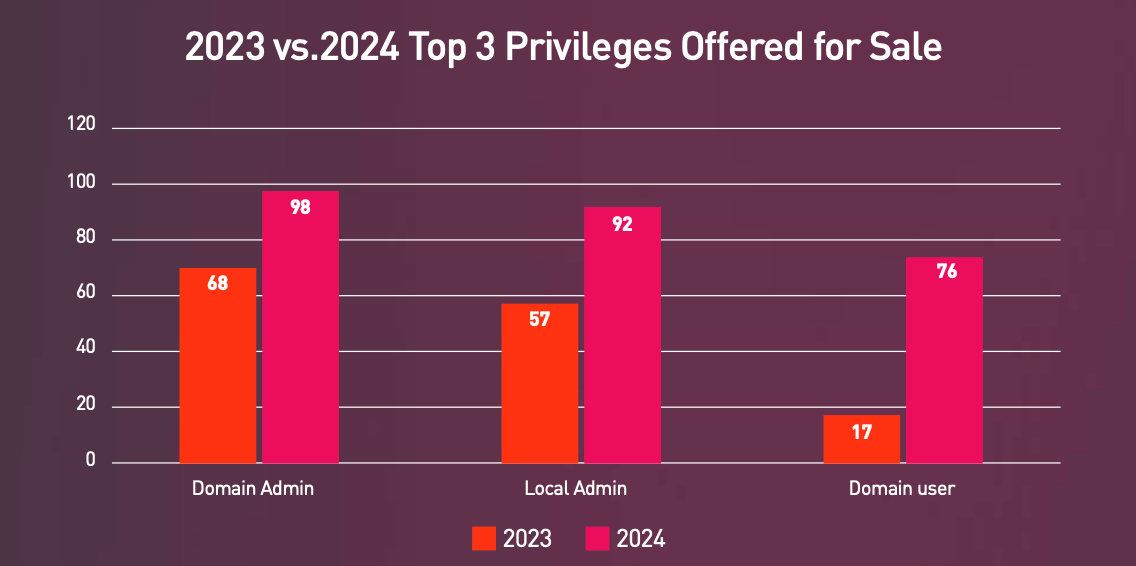
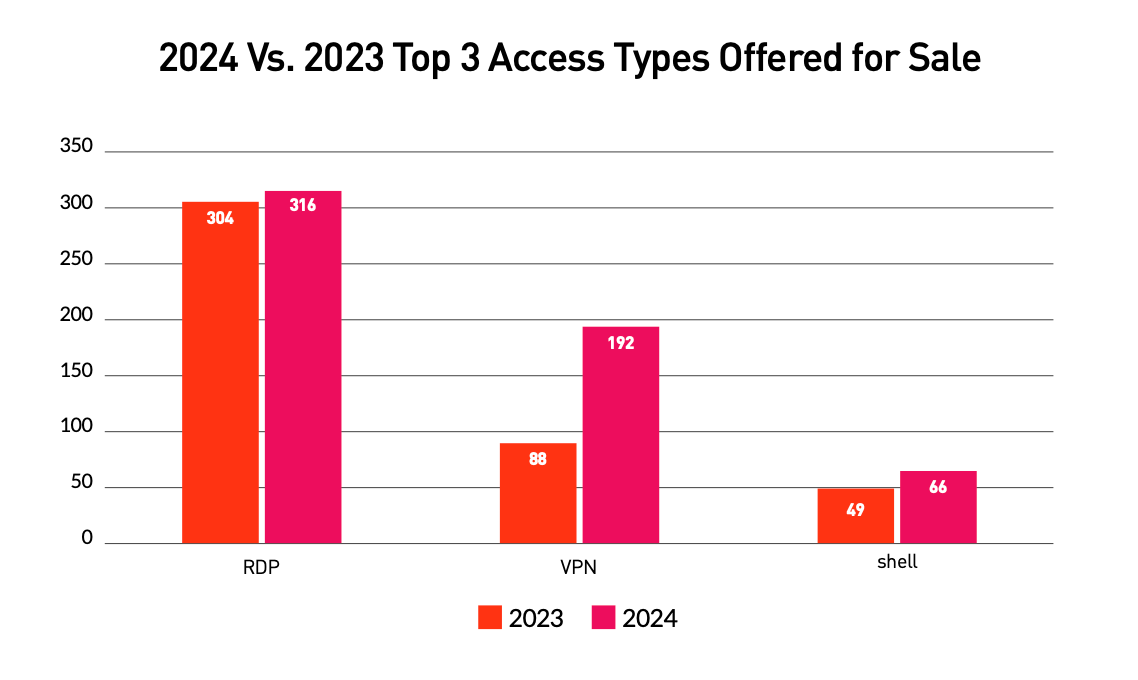
There are three primary types of IABs driving most ransomware attacks.
In 2023, the most popular form of attack was servers compromised through exposed Remote Desktop Protocol (RDP), which accounted for 60% of listings.
Today, RDP still holds the top spot with 55% of activity but is being challenged by VPN access (33%) due to the rise of remote working.
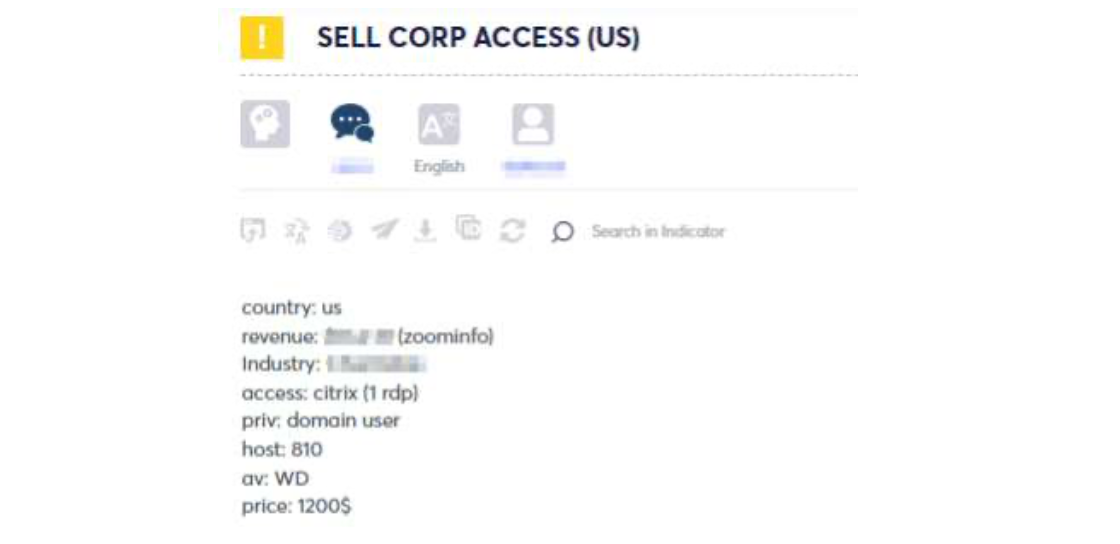
Most IAB posts charge between $500 to $3,000 for corporate access, although high-value listings costing $10,000 are also seen "occasionally".
Just over half (53%) of compromised endpoints involved Windows Defender, which reveals "poor investment in layered security".
Meet "Mommy": An East Asian Initial Access Broker
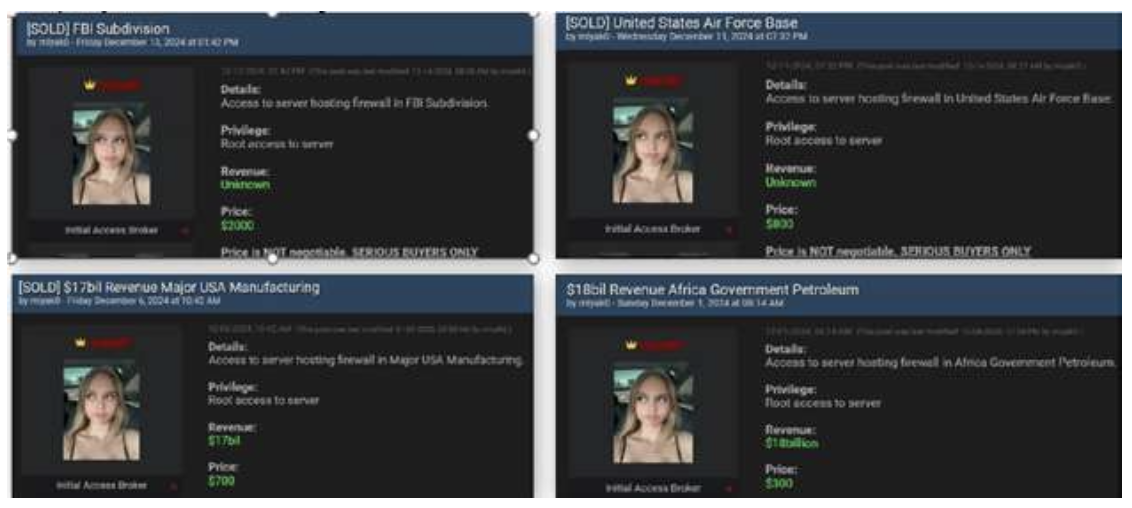
The report revealed details of a group nicknamed Miyako - which is also known as "mommy". Its name refers to the Japanese term for "capital" or "city", indicating that it specialises in targeting critical infrastructure within urban and capital regions.
IAB is connected to East Asian cybercriminals and state-affiliated organisations, indicating a "dual motivation" of financial gain and nation-state level espionage.
It does not attack nations in the Commonwealth of Independent States, an alliance of countries formed around Russia after the collapse of the Soviet Union.
However, Miyako does target many industries, including energy, retail, finance, telecom, education, healthcare and government in countries around the world, such as the USA, China, France, and Indonesia.
It recently leveraged CVE-2022-1388, a critical authentication bypass vulnerability in F5 BIG-IP devices, to attack one target. After the compromise, another group called Hellcat launched a ransomware attack on the company, demanding $150,000 in Monero or Bitcoin.
"This is just one example of the tight intertwined relationship between IABs and ransomware threat actors," Check Point wrote. "The link to Hellcat highlights that Miyako’s primary motivation was financial. However, the public access listings he’s currently offering for sale suggest a shift in intent—one that appears more ideological and potentially tied to nation-state activity or influence."
How to protect against IABs
Check Point offered the following advice:
- Enforce multi-factor authentication across all remote access points.
- Limit and monitor exposed services like RDP and VPN.
- Deploy layered endpoint protection beyond default tools like Windows Defender.
- Regularly audit credentials and user permissions.
- Use threat intelligence to monitor for mentions of your company on underground forums.
Have you got a story or insights to share? Get in touch and let us know.




