Five advanced email attacks to fear in 2025
"As the front door of an enterprise and the gateway employees rely upon to do their jobs, the inbox represents an ideal access point for attackers."

Email inboxes are the frontline of an organisation's defences and remain a major attack vector.
Invented more than four decades ago, email offers threat actors a route right into the heart of an organisation and a method of targeting one of its most glaring weak points: human employees.
To help businesses prepare for next year's threats, the cloud email security firm Abnormal has issued a briefing about five advanced email attacks that defenders should prepare to deal with in 2025 - also sharing real-life examples from its customers.
"While cybercriminals can (and do) infiltrate organisations by exploiting software vulnerabilities and launching brute force attacks, the most direct - and often the most effective - route is via the inbox," it wrote.
"As the front door of an enterprise and the gateway employees rely upon to do their jobs, the inbox represents an ideal access point for attackers. And it seems that, unfortunately, cybercriminals aren’t lacking when it comes to identifying new ways to sneak in."
Here are the five attacks to look out for over the next year.
Cryptocurrency fraud
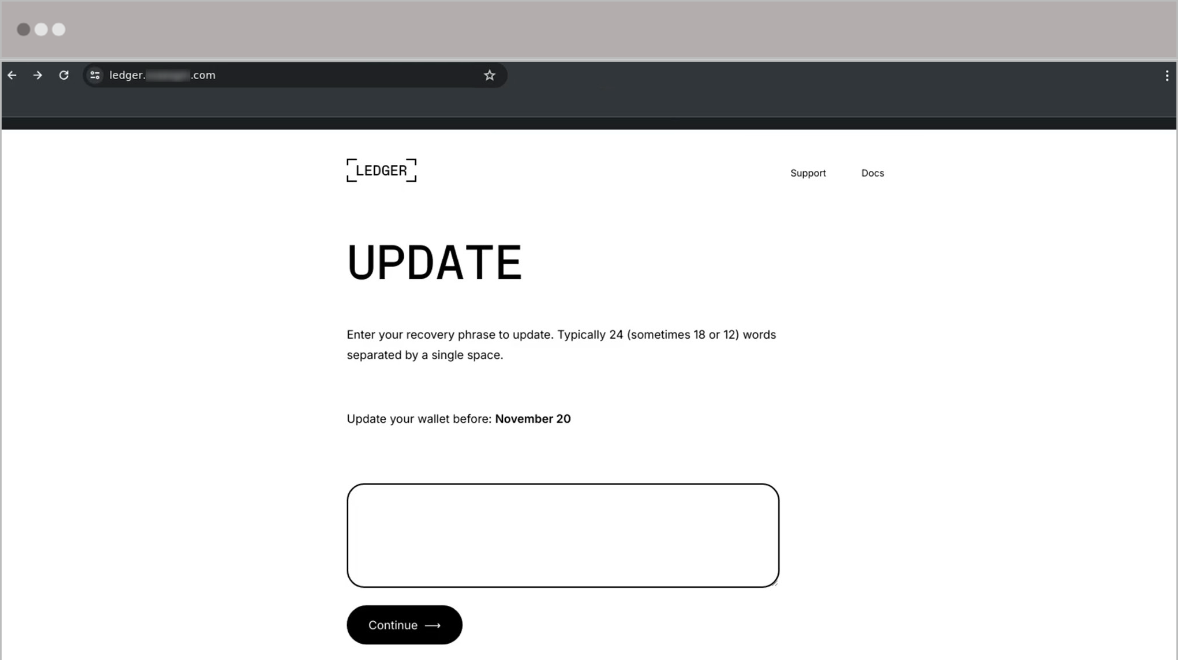
The image above shows a fake email designed to trick victims into handing over the recovery phrase that enables access to their crypto accounts.
While most people would never anyone their mother's maiden name or some other piece of information used to get into bank accounts, a lack of understanding around crypto makes this type of fraud more likely to be successful.
Additionally, traditional security solutions such as secure email gateways (SEGs) would often fail to identify an email like this as malicious, Abnormal warned.
In one attack, attackers used a 30-year-old domain to bypass legacy systems that "equate age with trustworthiness", as well as a domain belonging to a legitimate business to sidestep defences.
"Plus, the sender had never communicated with the recipient before—a challenge for SEGs, which often struggle to assess the risk of new senders accurately," the security firm continued.
The FBI's most recent stats show that this attack method caused losses of $5.6B in 2023.
File-sharing phishing
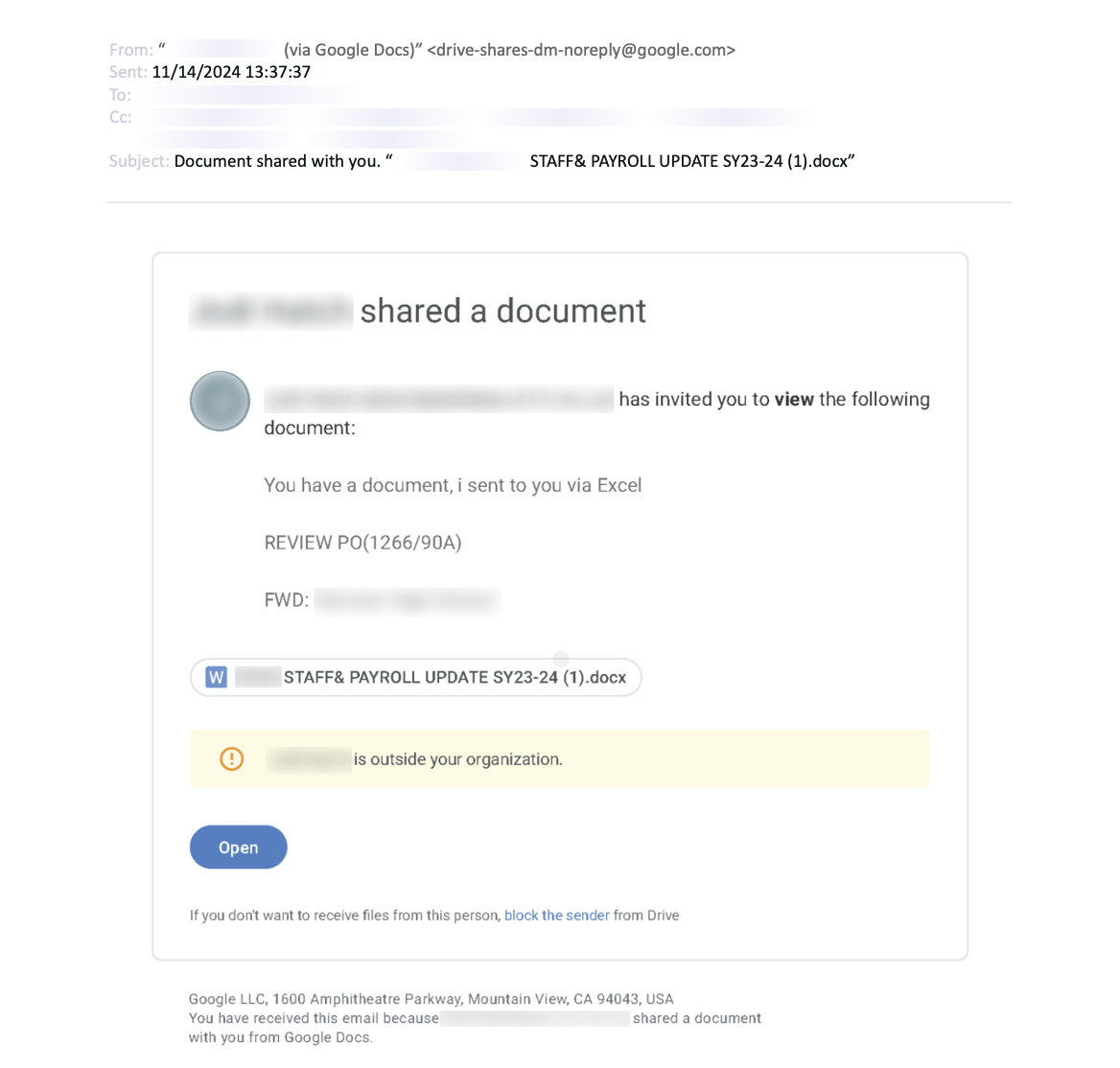
Abnormal identified a 350% increase in file-sharing phishing attacks between June 2023 and June 2024.
This attack involves threat actors exploiting legitimate file-hosting sites and then persuading victims to download documents laced with malicious links.
By starting accounts with services like Dropbox, attackers can send large numbers of emails that appear legitimate and are more likely to be convincing.
"Unlike the vast majority of phishing attacks, the malicious link isn’t contained within the email," Abnormal wrote. "It exists within a separate document hosted on a genuine file-hosting service, and it’s only after the target leaves the email environment and engages with the shared file that they’re exposed to the phishing link."
Multichannel phishing
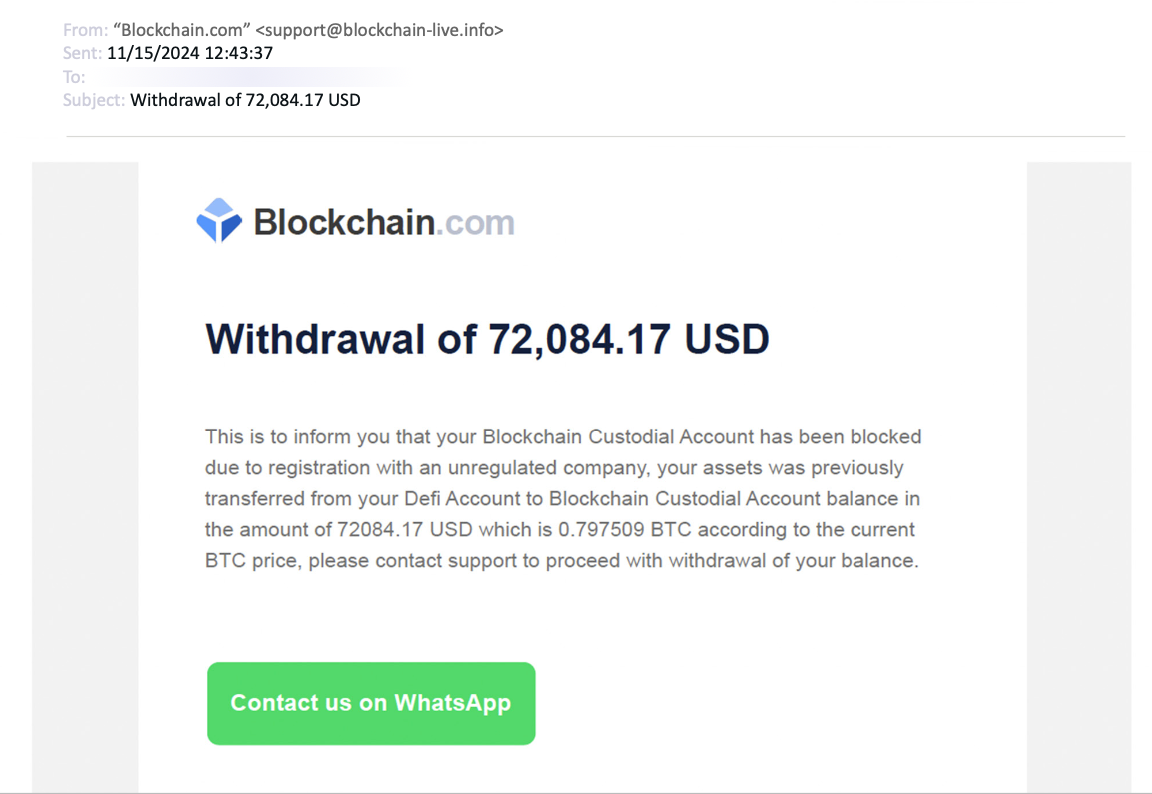
This is an attack that starts in one channel, before drawing people into another.
"Multichannel phishing represents an evolution of phishing tactics, leveraging multiple communication platforms to manipulate victims more effectively," Abnormal wrote.
Unlike traditional phishing, multichannel attackers first make contact via email but then try to lure their target into other channels, such as phone calls, text messages, or third-party messaging apps like WhatsApp or Telegram.
This strategy "fosters a sense of urgency by transitioning from an asynchronous channel to a real-time medium" and "increases the probability of deceiving employees since security awareness training primarily focuses on the email environment". It also moves the interaction from company computers to users' personal devices, bypassing enterprise security protections.
AI-generated business email compromise
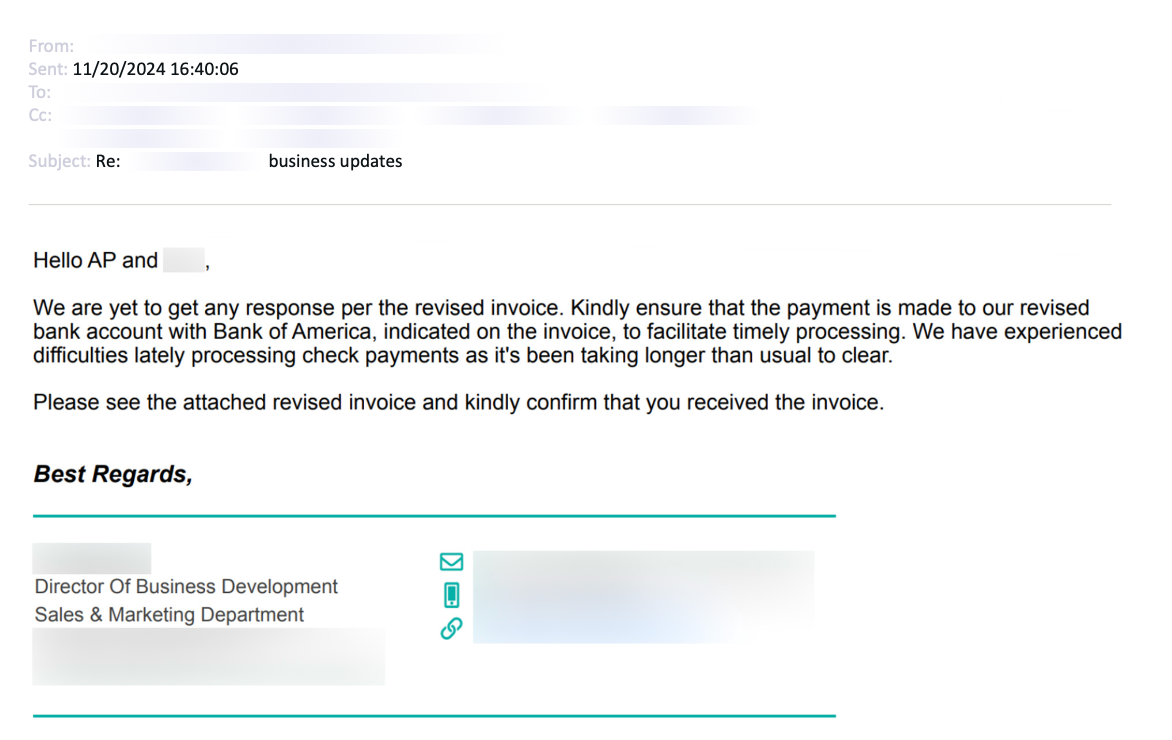
Artificial intelligence is putting a new face on an old threat. It has never been easier and faster to generate highly convincing emails that appear to come from a senior member of staff.
Abnormal warned: "By analyzing vast volumes of data from social media, online activity, and past interactions, AI-powered platforms can generate hyper-personalized messages that convincingly mimic the writing style of the impersonated individual. This makes the emails more difficult for traditional security measures to detect and more likely to deceive unsuspecting recipients."
The email above was sent from the compromised account of the Director of Business Development at a renewable energy manufacturer, asking for an invoice to be settled. Had the person who received this message sent the money, the business would've been down by $250,000.
"Thanks to GenAI, the email has no misspellings and uses acceptable grammar, punctuation, and syntax," Abnormal wrote. "And because it was sent from the director’s real account, the recipients have no reason to believe the request is fraudulent."
Email account takeover
"This may be the most dangerous email threat that organisations face, as it provides threat actors with unparalleled access to the company’s network and internal systems," Abnormal warned.
It can be initiated by phishing, social engineering, password stuffing, or session hijacking via authentication token theft or forgery.
"These attacks are especially insidious because they enable bad actors to weaponise an account’s existing reputation, making malicious activities more difficult to detect," Abnormal wrote. "By compromising a legitimate email account, cybercriminals can bypass traditional security measures and exploit the trust inherently placed in the account’s communications."
This creates a "highly effective and versatile attack vector" capable of enabling fraud in other areas throughout the company.
The average cost of a data breach caused by compromised credentials has now reached $4.81 million.
Have you got a story to share? Get in touch and let us know.




