Who hacked X? Dark Storm Team claims responsibility for monster DDoS attack
Rumours swirl after the social network formerly known as Twitter was brought down by a huge cyberattack.
A pro-Palestinian hacker group known as Dark Storm Team has claimed responsibility for a huge DDoS attack that brought down X.
The group is understood to have formed in 2023 and previously targeted websites belonging to governments from Israel and supporting NATO countries.
However, X owner Elon Musk has linked the incident to Ukraine, which is locked in a diplomatic spat with Washington after Zelensky's disastrous visit to the White House - where he locked horns with Trump and was reportedly kicked out.
The DDoS attack hit yesterday and was so severe it caused X outages around the world.
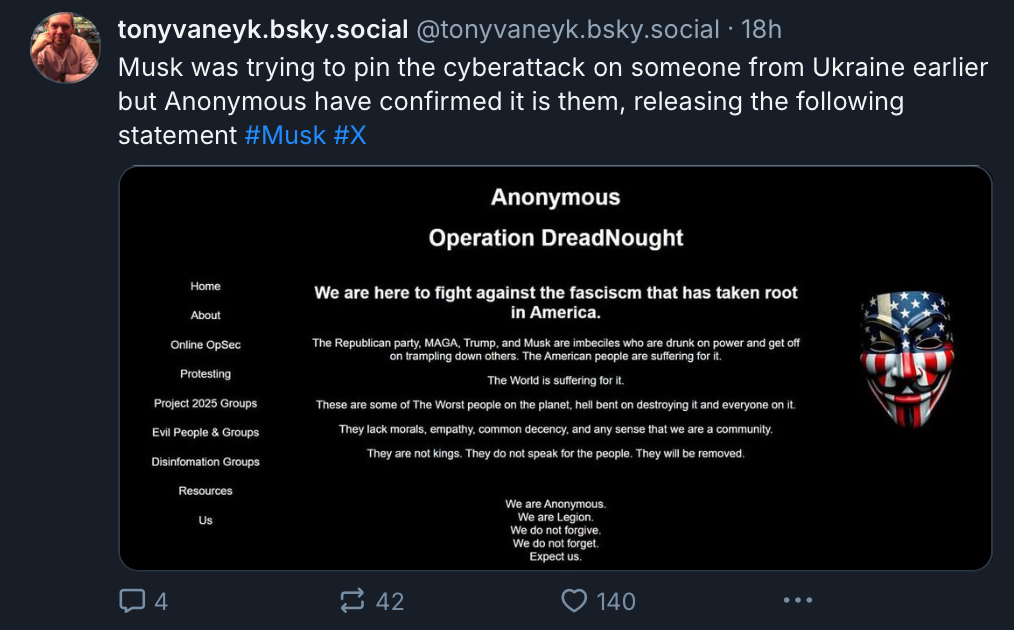
It was welcomed by Musk's ideological enemies on rival social media network Blue Sky, who immediately pinned the blame on Anonymous.
Yesterday, Musk tweeted: "There was (still is) a massive cyberattack against 𝕏.
"We get attacked every day, but this was done with a lot of resources. Either a large, coordinated group and/or a country is involved."
In an interview with Fox Business, he later said: "We're not sure exactly what happened, but there was a massive cyber attack to try to bring down the X system with IP addresses originating in the Ukraine area."
Since then, groups including Antifa and Anonymous have been blamed for the incident, although a group of pro-Palestine hackers called Dark Storm Team took responsibility in a group on Telegram that has since been shut down. A new profile claiming to speak on behalf of Dark Team is now sharing screenshots of stories about its alleged escapades.
Check Point Research (CPR) also attributed the incident to Dark Storm, reporting that it has "re-emerged after a period of inactivity following the takedown of their Telegram channel."
The group's primary targets have included Western entities, including organisations in the United States, Ukraine, the UAE, and Israel. Over the past month, they have launched successful attacks on critical infrastructure, including LAX in the US, Haifa Port in Israel and the UAE's Ministry of Defense.
Check Point Research said: "The Dark Storm Team has taken credit for the assault on X, consistent with their broader goal of destabilising prominent digital platforms and infrastructure. This event highlights the essential need for strong cyber security protocols for social media platforms, which play a key role in worldwide communication."
Oded Vanunu, Chief Technologist, WEB 3.0 & Head of Product Vulnerability at Checkpoint added: "The resurgence of Dark Storm Team highlights the growing cyber threat against major online platforms and critical infrastructure."
Is Dark Storm Team a mercenary group of hacktivists for hire?
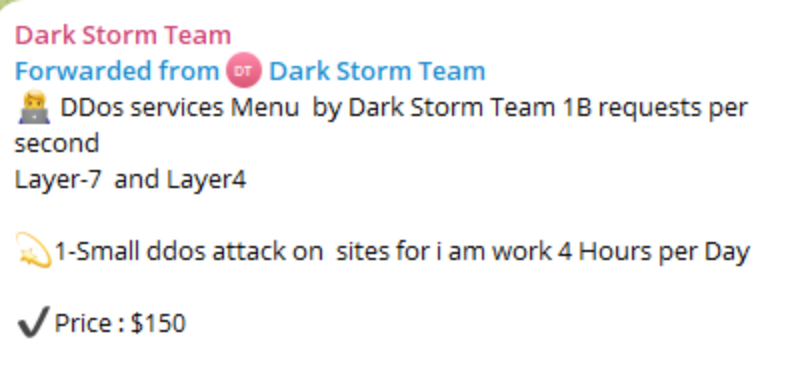
Field Effect, a cybersecurity firm, said the attack might have been launched on behalf of a paying client. It alleged Dark Team could be hired as a cyber-mercenary to do the dirty work of unnamed individuals or shadowy organisations.
It wrote: "Dark Storm Team has, for nearly a year, been openly advertising its DDoS-for-hire services. Cybercriminal groups frequently engage in such activities, offering their botnets to third parties for financial or ideological motives.
"Given this, it's plausible that Dark Storm did not target X out of its own initiative but instead acted on behalf of a paying client. The timing of the attack aligns with increased political pressure on Elon Musk, particularly regarding his involvement in U.S. government policy and his role in the Department of Government Efficiency."
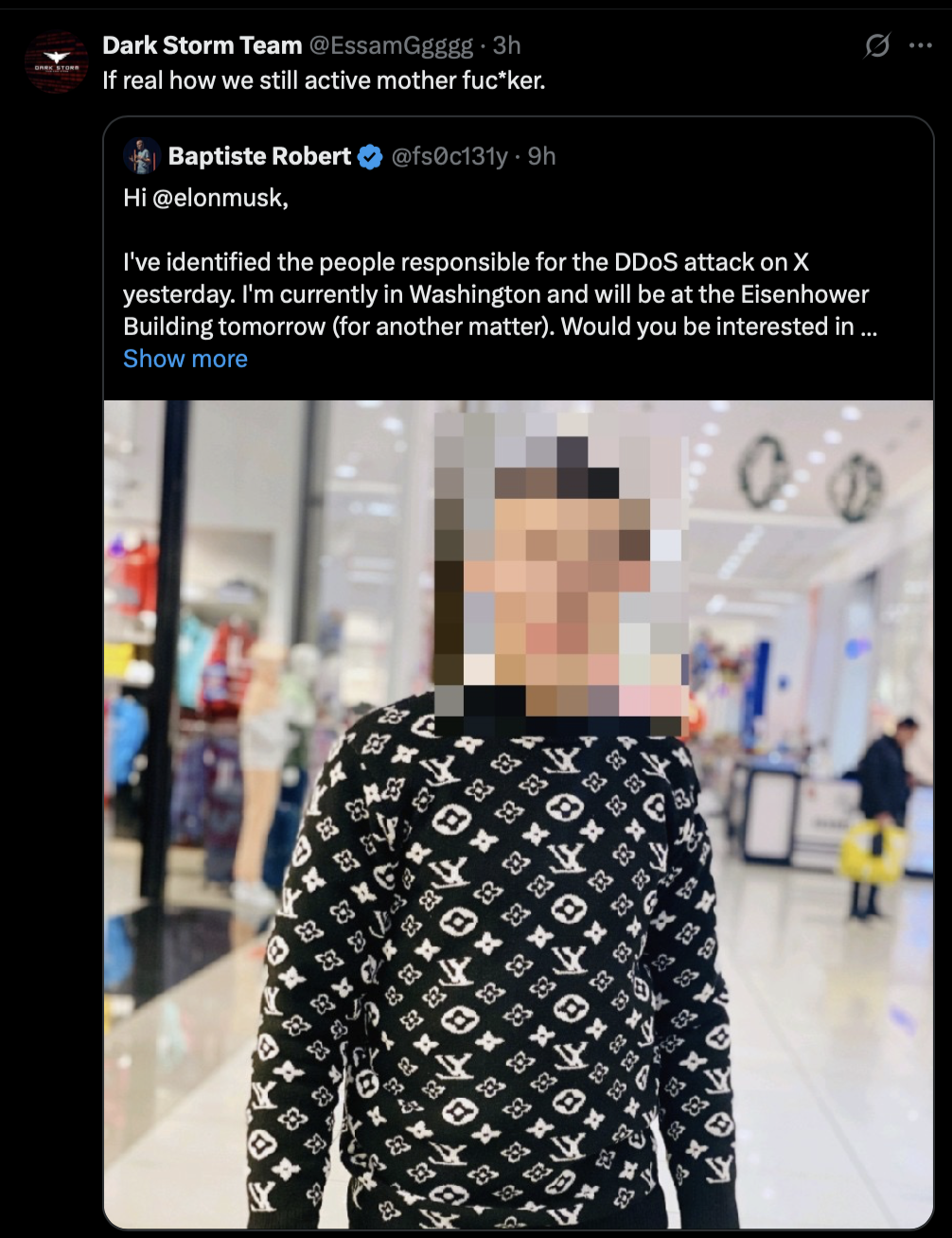
Baptiste Robert, CEO of Predicta Lab, also claimed the leader of Dark Storm Team posted on a Telegram page advertising "DDoS attack services".
He tagged Elon Musk into a thread on X, which shared the results of his open source intelligence (OSINT) investigation into Dark Storm and alleged that its leader is a young student living in Giza.
An X account claiming to belong to Dark Storm Team was quick to deny the claims.
"Lol fake mother fucker," it wrote.
Podcaster and internet personality Ed Krassenstein later said he'd spoken to Dark Storm (dropping the team bit of the name).
He wrote: "They tell me that the IPs did not originate from Ukraine, and that they 'can attack again'. A stronger attack this time.
"They also said that they can attack Tesla as well, and that Elon Musk 'must provide evidence for his claim,' regarding Ukraine, as they adamantly deny this to be the case."
The group does appear to be at least ideologically linked to Anonymous, which has been waging its own campaign against President Trump and Elon Musk.
The main Anonymous X accounts have all tweeted support for the DDoS attack - although this does not prove any actual affiliation.
Realistically, Anonymous is no longer the group it once was and is now significantly smaller and more partisan than its classic incarnation (although it's hard to say anything completely certain about an amorphous collective of nameless members).
So although Anonymous supporters want you to believe that Elon is lying about the attack's link to Ukraine, we cannot be certain who is telling the truth at this stage - and may never be 100% sure.
Stay tuned to Machine for more updates.
Have you got a story or insights to share? Get in touch and let us know.




