Huge surge in number of CVEs exploited in the wild blamed on complex ecosystems
Researchers warn that 2024 was a "banner year" for threat actors, who are exploiting vulns at a dizzying speed.

The number of CVEs reported to have been exploited in the wild accelerated dramatically last year by 20% YoY to more than 760.
Analysis from VulnCheck identified a huge "spike" in recorded CVEs throughout 2024 linked to "key industry events", as well as a rise in the number of unique sources of vulnerabilities.
More than 100 companies were the first to report a CVE, with third-party vendors leading the charge, including security companies like CheckPoint, Aqua Security, Fortinet, and F5, along with government agencies such as DoD, CISA and the NHS) and non-profits, including Shadow Server.
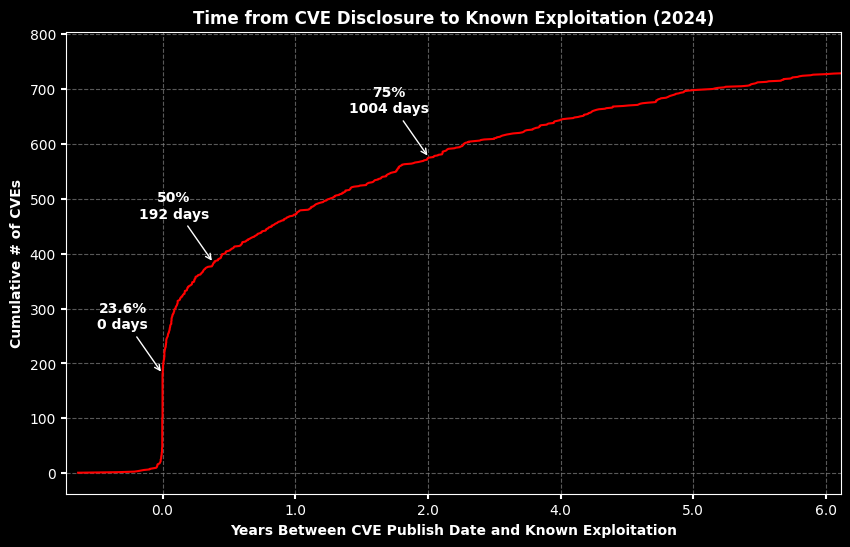
In 2024, 23.6% of KEVs (known exploited vulnerabilities) were known to be exploited on or before the day when CVEs were publicly disclosed.
Patrick Garrity, a VulnCheck security researcher, said 2024 was "another banner year for threat actors targeting the exploitation of vulnerabilities".
"Exploitation disclosures came from various sources, including product companies, security vendors, government agencies, non-profits, and media outlets worldwide," he wrote.

In 2024, VulnCheck identified 768 CVEs that were publicly reported as exploited in the wild for the first time. This is an increase from 2023, which saw 639 CVEs targeted.
During 2024, 1% of the CVEs published were exploited. This number is expected to grow as exploitation is often discovered long after a CVE is published.
There was a big surge during April and May during the RSA conference and around the publication of companies' quarterly reports.
"These spikes underscore how industry events and new resources impact reporting volumes on exploitation," Garrity added. "We encourage organizations to publicly disclose any instances where there is exploitation activity."
Vulnerabilities are now being exploited terrifyingly quickly after disclosure. In 2024, 23.6% of KEVs were exploited on or before the day their CVEs were publicly disclosed, a slight decrease from 2023's 27%.
"Despite the buzz around 'zero-day' exploitation, these findings indicate that exploitation can happen at any time in a vulnerability's lifecycle," Garrity warned.
Of the 768 CVEs first reported as exploited in 2024, 112 unique sources provided initial evidence, including big names like Ivanti, Cisco, Apple, Google, Microsoft and others, which frequently disclosed exploitation of their own products as well as third-party vulnerabilities.
VulnCheck admitted that there may be some bias in its research, as it onboarded ShadowServer over a three-month period starting in November 2023.
"Several of these CVEs are likely to have been identified prior to us adding this as a source so there is likely an increase in the number of CVEs associated with Shadow Server that could be attributed to an earlier date," it wrote.
"It’s possible there are other resources for public exploitation that we haven’t captured."
Glenn Weinstein, CEO of Cloudsmith, blamed the surge partly on the rise in ecosystem complexity.
“This surge in CVE exploitation highlights a key vulnerability in modern software development: speed," he said. "Attackers aren’t waiting and organizations can no longer afford to either.
"New vulnerabilities are emerging as software ecosystems grow more complex, which has created a larger attack surface. Proactive measures, such as policy enforcement and vulnerability scanning, remain critical to mitigating risks from newly disclosed vulnerabilities, limiting the window of exposure.
"Proactive security measures like policy enforcement, automated vulnerability scanning, and continuous CVE tracking are critical to limiting the damage from newly disclosed vulnerabilities.”
Have you got a story or insights to share? Get in touch and let us know.




