China's secret surveillance tool has a strange limitation
Sinister spy software lets cops collect "extensive sensitive data" from people's phones and snap pictures from their camera

Chinese police officers have access to an advanced surveillance tool that appears to be missing one critical feature.
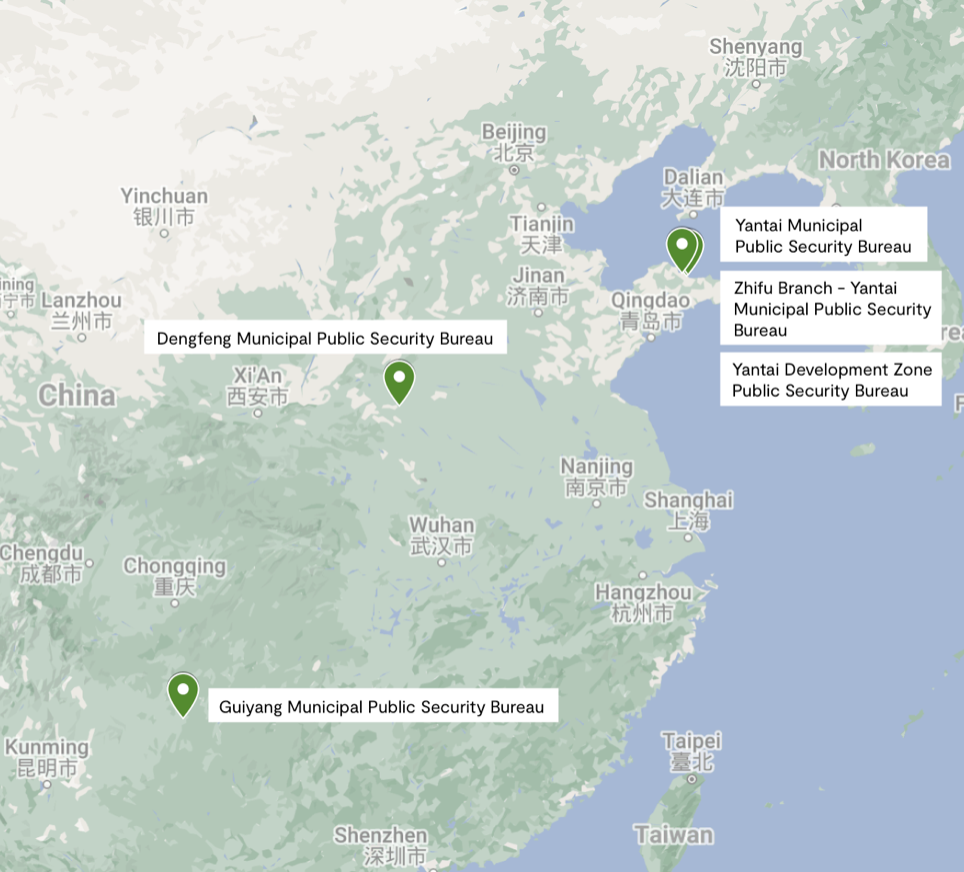
Researchers from Lookout discovered a "lawful intercept surveillance tool" called EagleMsgSpy that public security bureaus (police stations) use to monitor citizens and criminals across mainland China.
It is believed to be in contact with other Chinese surveillance apps, forming a sinister spy network across the People's Republic.
A sample of CarbonSteal - a surveillance tool discovered by Lookout and attributed to Chinese APTs (advanced persistent threats that are often state-sponsored threat actors) was observed communicating with another IP tied to the EagleMsgSpy SSL certificate.
In a previous threat advisory in 2020, Lookout researchers identified CarbonSteal activity in campaigns targeting minorities in China, including Uyghurs and Tibetans.
"Significant overlap in signing certificates, infrastructure and code was observed between CarbonSteal and other known Chinese surveillance, including Silkbean, HenBox, DarthPusher, DoubleAgent and PluginPhantom," Kristina Balaam, Staff Security Intelligence Engineer at Lookout warned.
A Chinese software development company is understood to have developed the spy tool, which has been in use since at least 2017.
The "surveillanceware" consists of two parts: an installer APK and a surveillance client that runs headlessly on the device.
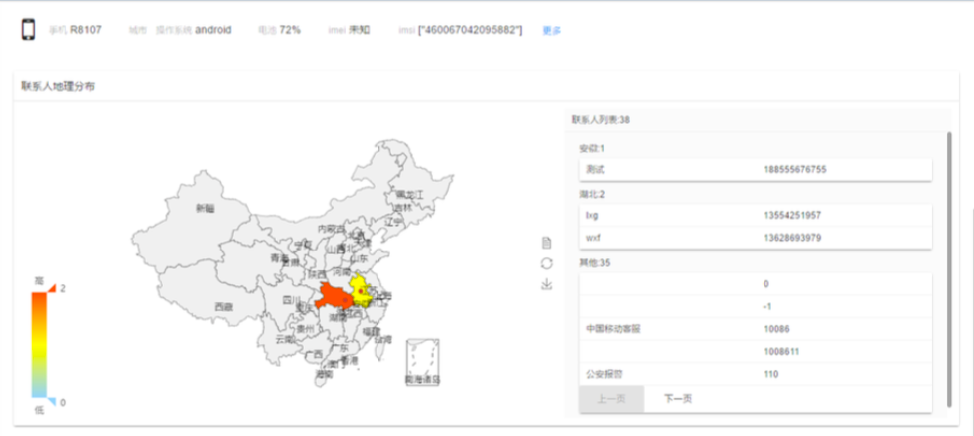
EagleMsgSpy is capable of collecting a significant amount of data from Android devices, including call logs, screen recordings, screenshot captures, audio files, text messages, location data and network activity.
Although internal documents obtained from open directories on attacker infrastructure "allude to the existence of an iOS component", this has not yet been discovered.
Lookout researchers uncovered two documents that direct users to help files summarising how to use the tool.
These pages describe it as a “comprehensive mobile phone judicial monitoring product” that can obtain “real-time mobile phone information of suspects through network control without the suspect’s knowledge, monitor all mobile phone activities of criminals and summarize them”.
The user manual explains that cops can use EagleMsgSpy to trigger "real-time photo collection from a device, real-time screenshot collection, block incoming and outgoing calls and SMS messages to specific phone numbers, and initiate real-time audio recording from the device."
So what's the spy software missing? The ability to infect devices over the internet.
EagleMsgSpy "appears to require physical access to the device to initiate surveillance operations", Lookout wrote.
The surveillenceware must be installed through a QR code or physical device that can install the client when connected to USB.
"An installer component, which would presumably be operated by law-enforcement officers who gained access to the unlocked device, is responsible for delivering a headless surveillance module that remains on the device and collects extensive sensitive data," Balaam wrote.
"We believe that this is the only distribution mechanism and neither the installer nor the payload have been observed on Google Play or other app stores."
Read the full report, including indicators of compromise.
Have you got a story to share? Get in touch and let us know.
Follow Machine on X, BlueSky and LinkedIn




