Los Angeles wildfire phishing scammers use "cancer-stricken dogs" to defraud good Samaritans
"Natural disasters like the LA fires of 2025 let cybercriminals exploit the vulnerabilities of human psychology"
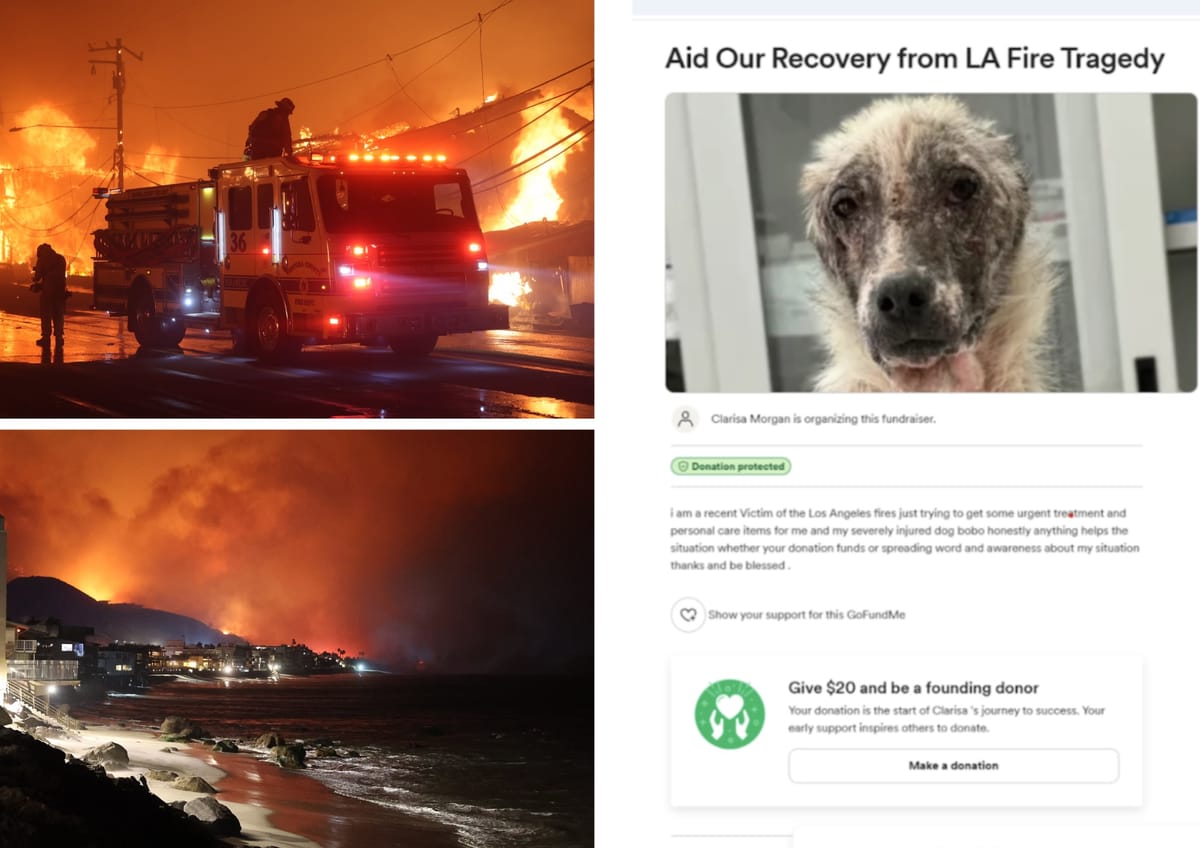
Cold-hearted fraudsters are scamming charitable folks by posing as victims of the Los Angeles wildfire and manipulating them into making donations.
That's just one example of the cynical criminal tactics uncovered in an investigation from predictive cybersecurity specialist BforeAI, which explored the shocking and sometimes low-tech methods criminals use to pull on victims' heart and purse strings.
Researchers uncovered multiple phishing campaigns centred around themes such as insurance, fundraising, claims, restorations, and the fire department.
They even found people using pictures stolen from a previous fundraising campaign for a cancer-stricken dog, claiming it showed a much-loved pet that had been caught in the blaze and asking people to urgently send funds to pay for treatment.
"Natural disasters like the Los Angeles wildfires of 2025 often create an opportunity for cybercriminals to exploit the vulnerabilities of human psychology," researchers wrote.
"We discovered multiple threats surrounding the recent natural calamity in Los Angeles, California."
Fake domains and very real consequences
Swindlers registered vast numbers of scam domains registered as Los Angeles burned. BforeAI analysed 119 of these which were registered between January 8 and 13, 2025 across various registrars.
It's claimed that 58% of the domains were registered through GoDaddy, making it the most commonly used registrar in this campaign, followed by Namecheap and Register. Other prominent domain registrars included Ionos, Hostinger, Squarespace, Tucows, etc.
The domains primarily targeted keywords such as “LA fire,” “wildfire,” “relief,” “fund,” and “rebuild".
"All were registered in a short frame of time once the incidents started gaining significant coverage in the media and sympathetic responses from people around the world," researchers wrote.
The most prevalent top level domain (TLD) was “.com”, accounting for 70% of the total, followed by “.org”, and “.net”. Some of the domains also used “.fund”, hinting they were trying to pose as a financial firm or campaign, while others attempted to establish the credibility of the domain by using popular TLDs.
Some of the domains target human emotions and triggers, such as the name “findmypetlafires.com”. Others helped crooks claim involvement in financial recovery efforts like “lafireinsuranceclaims.com" or "lafirelegalhelp.com".
As well impacting victims, the LA fire scams have a wider effect, polluting the information ecosystem and causing noise which can hurt the visibilty of genuine campaigns.
Tactics of the LA fire scammers
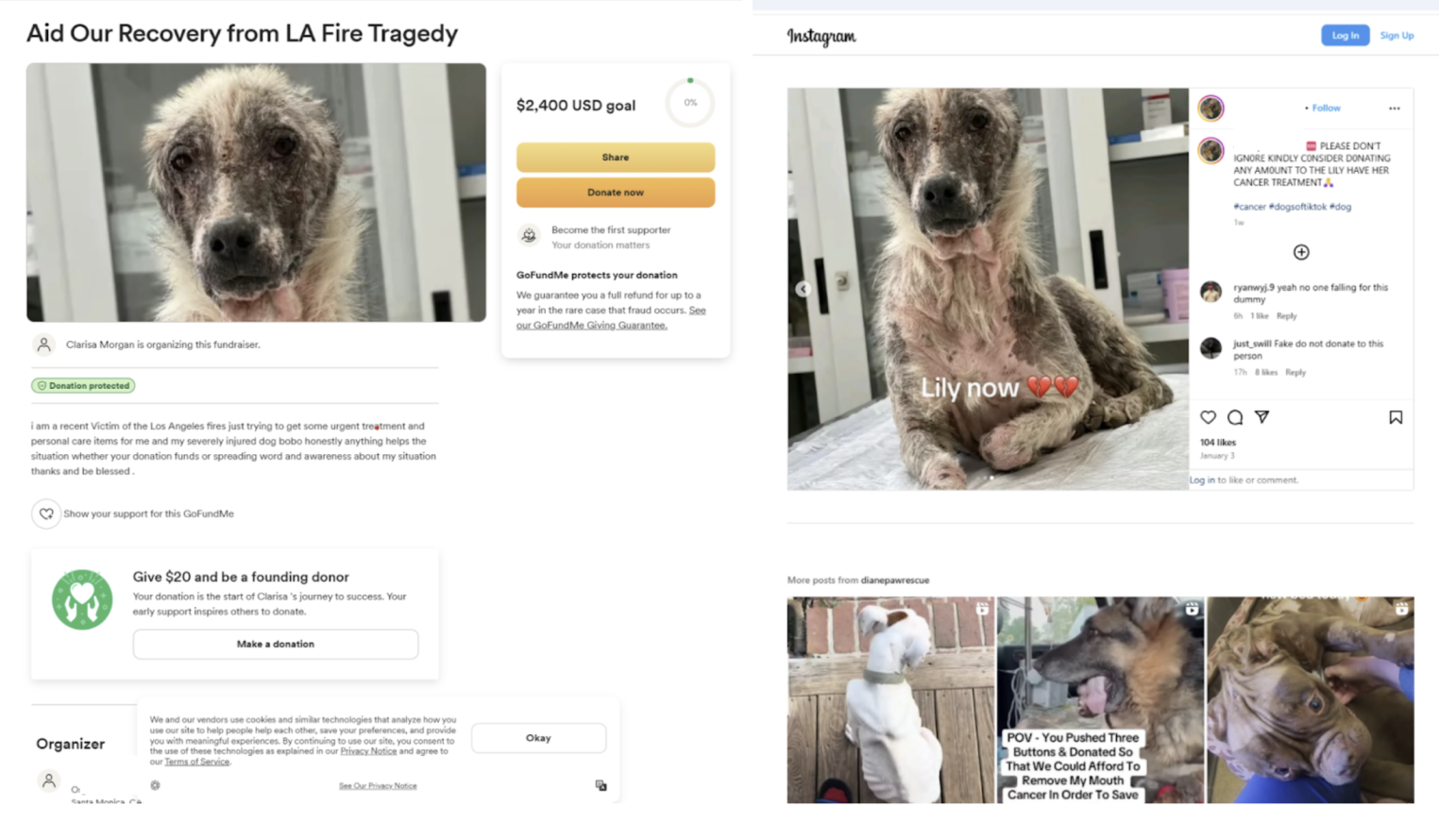
A range of fake pet-focused fundraisers have also been posted to donation sites likes GoFundMe, which use pictures from previous tragic incidents to trick good Samaritans.
One scammer created a GoFundMe for a dog called: "Aid Our Recovery from LA Fire Tragedy”.
However, the "burned dog" in the image was actually taken from another alleged scam campaign which claimed it was "cancer-stricken".
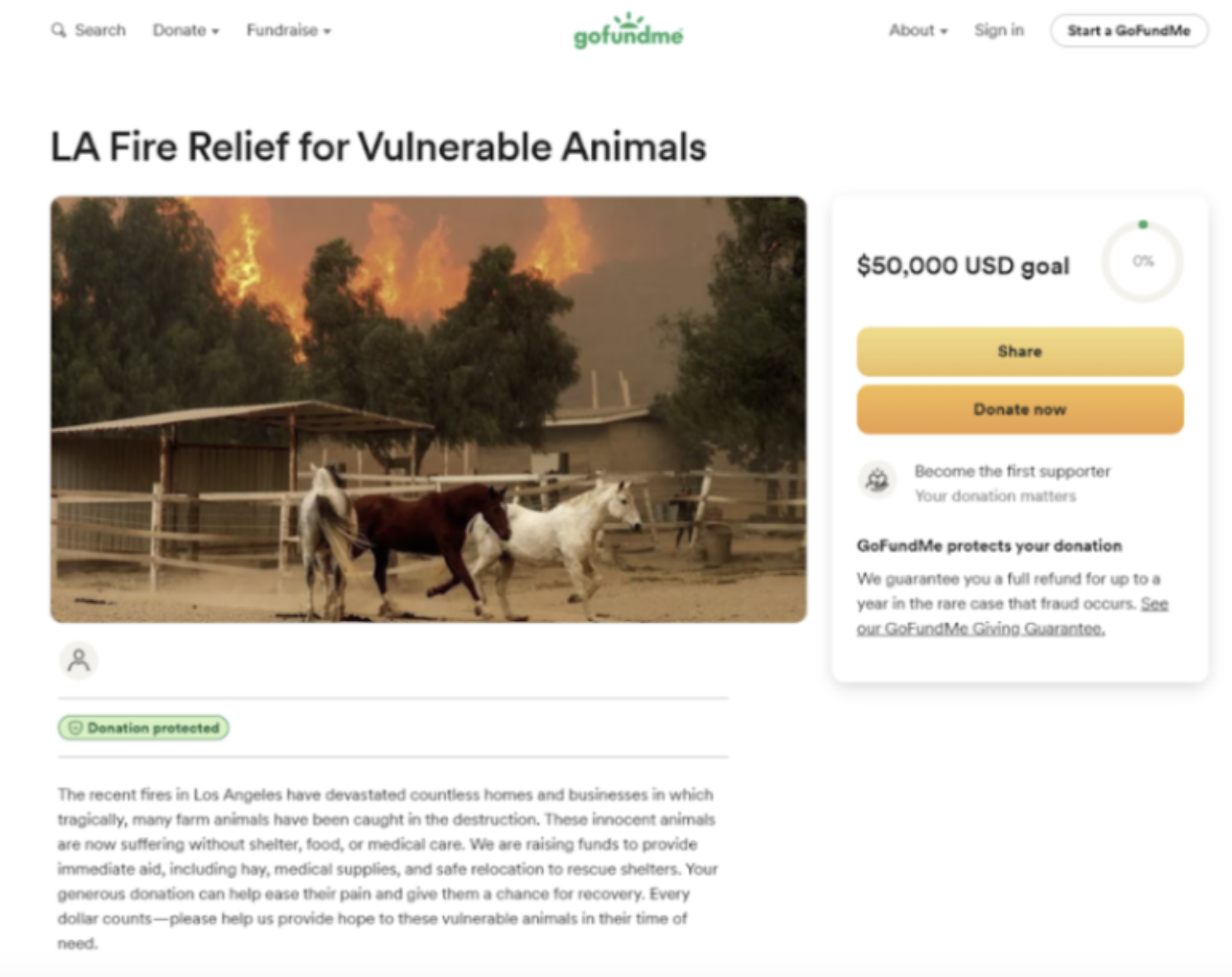
Similarly, another instance of a GoFundMe claimed to be a campaign called "LA Fire Relief for Vulnerable Animals" but used an image taken during a previous incident in November 2024 - long before the fires ignited.
At least eight fraudulent GoFundMe campaigns have been identified, using recycled images and deceptive tactics to steal money or data to enable further scams.
Investigators exposed fake aid websites that harvest personal and financial information and misleading “informational” pages designed to spread panic and misinformation.
There has even been a surge of newly minted fire-themed crypto-coins - some linked to "get-rich-quick” traps . These “pump and dump” schemes exploit social media to reach bigger audiences and target vulnerable people.
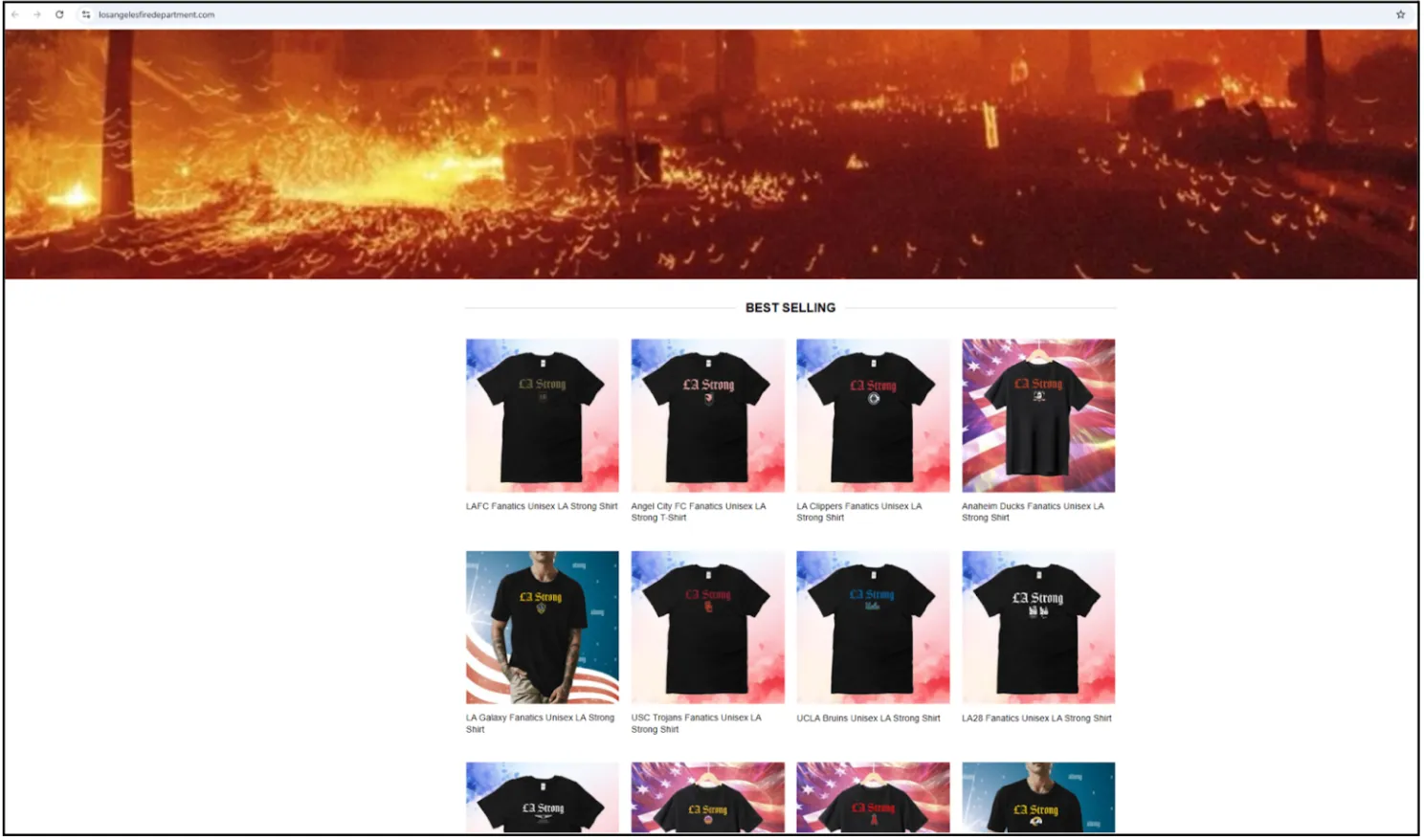
Merchandise scams have also emerged, with fraudulent websites claiming to sell apparel and goods under the name of the Los Angeles Fire Department. These sites mislead charitable consumers by falsely associating their efforts with official organisations.
Hurricane Helene hoaxes vs LA fire scams
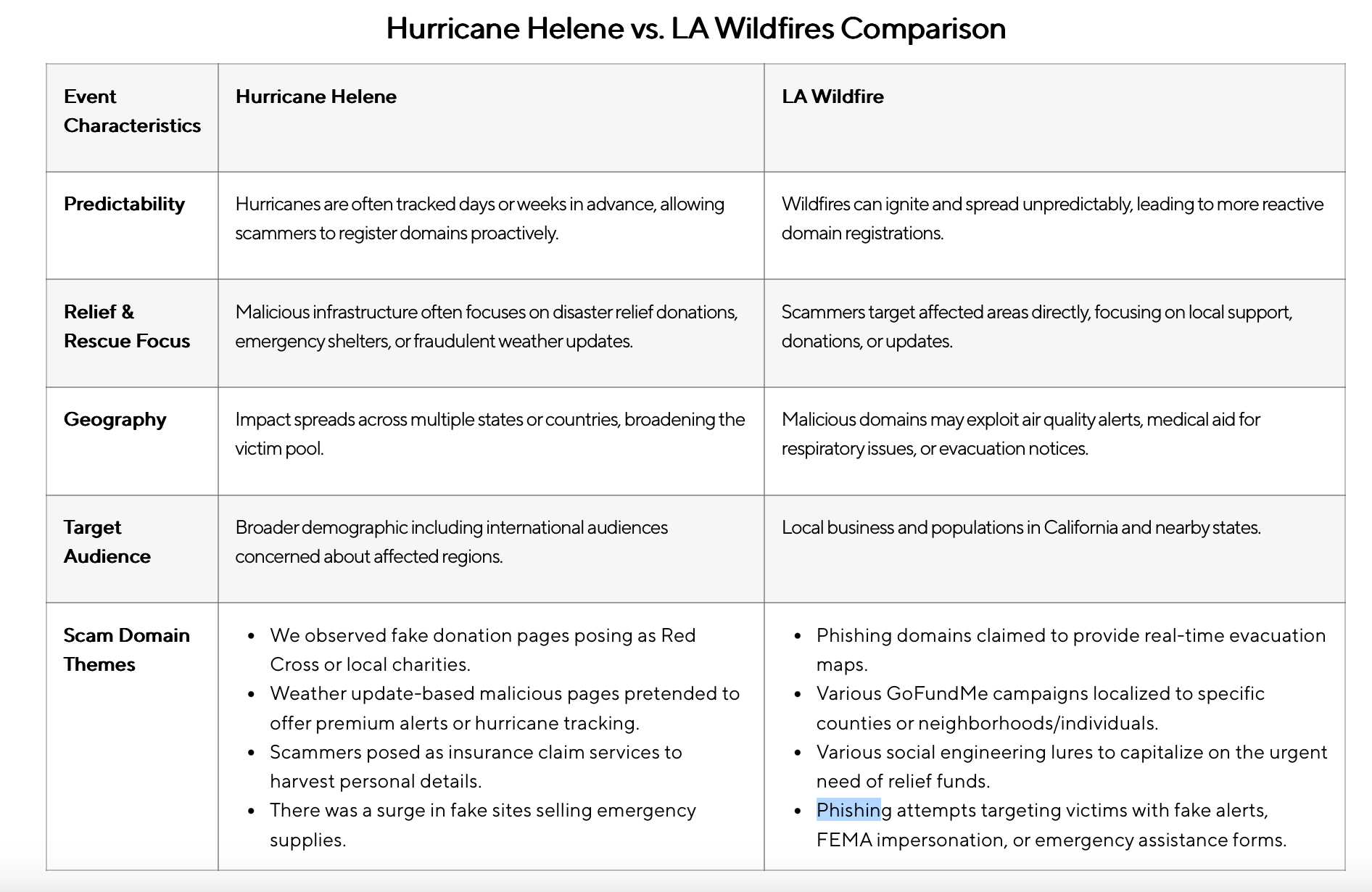
One of the most interesting parts of the report was its comparison between the ways scammers behaved during the fires and another disaster, Hurricane Helene in September 2024 - which we've screenshotted above.
Hurricanes move predictably and their path can be forecasted days or weeks in advance, allowing scammers to register domains proactively. Wildfires ignite and spread chaotically, leading to reactive domain registrations.
During Hurricane Helene, criminals built malicious infrastructure that enabled campaigns focusing on disaster relief donations, emergency shelters, or fraudulent weather updates. This involved fake donation pages posing as Red Cross or local charities or weather update-based malicious pages pretending to offer premium alerts or hurricane tracking.
Scammers also posed as insurance claim services to harvest personal details and there was a surge in fake sites selling emergency supplies.
During the LA fire, as well as the previously mentioned scams there were phishing domains claimed to provide real-time evacuation maps, various GoFundMe campaigns localized to counties, neighborhoods or individuals as well as social engineering lures to capitalize on the urgent need of relief funds.
Phishing attempts targeted victims with fake alerts, impersonations of FEMA or false emergency assistance forms. Malicious domains also exploited air quality alerts, medical aid for respiratory issues, or evacuation notices.
BforeAI offered the following mitigation strategies:
- Fundraising platforms should enforce strict rules and robust processes to identify and remove fraudulent campaigns.
- Users must verify the legitimacy of fundraising websites and avoid donating through suspicious platforms.
- Continuous monitoring should be implemented to detect and prevent fake websites that attempt to steal personal or financial data.
- Always fact-check information before entering sensitive details, making payments, or clicking on links.
- Be cautious of unverified cryptocurrencies on trading platforms, and avoid engaging with social media accounts promoting such coins, particularly newer or unverified ones.
Have you got a story or insights to share? Get in touch and let us know.




