Bybit crypto heist: North Korean hackers blamed for biggest theft in history
Kim Jong Un's goons stole more than $1.5 billion in Ethereum, which may go towards funding his ballistic missile program.

It was the most audacious and profitable theft the world has ever seen. Now the record-breaking Bybit crypto heist has been attributed to a notorious North Korean threat actor called the Lazarus Group.
On February 21, 2025, at approximately 12:30 PM UTC , Bybit detected unauthorised activity within one of its Ethereum (ETH) cold wallets during a routine transfer of funds.
Cold wallets are offline, providing enhanced security for long-term cryptocurrency storage. When Bybit was sending the huge cash of crypto to a hot wallet connected to the internet for easy access and transactions, the transaction was "manipulated by a sophisticated attack" that altered the smart contract logic - code that defines how a smart contract executes actions in response to events on the blockchain.
It also masked the signing interface, which allows users to sign files or messages using keys or certificates.
More than 400,000 ETH and stETH worth more than $1.5 billion were then transferred to an unidentified address.
"We want to reassure our users that this was an isolated incident involving only the ETH Cold Wallet," Bybit wrote. "All other cold wallets and assets, including BTC, remain secure, and client funds are unaffected."
"We are working alongside leading blockchain forensic experts to trace the stolen funds and resolve the situation."
Ben Zhou, CEO of the exchange, later said it had replenished all the stolen funds and reassured users that other cold wallets were secure.
Attributing the Bybit theft
Crypto fraud investigator ZachXBT uncovered links between the Bybit hackers and the Lazarus Group after the stolen Bybit funds were transferred to an Ethereum address previously connected to the Phemex, BingX, and Poloniex hacks.
This allegation was later confirmed by blockchain security firm TRM, which wrote: "TRM has determined - with high confidence - that the Bybit hack was perpetrated by North Korean hackers. This assessment is based on substantial overlaps observed between addresses controlled by the Bybit hackers and those linked to prior North Korean thefts.
"In a single day North Korea's hackers nearly doubled the amount they stole in 2024 (roughly $800 million)."
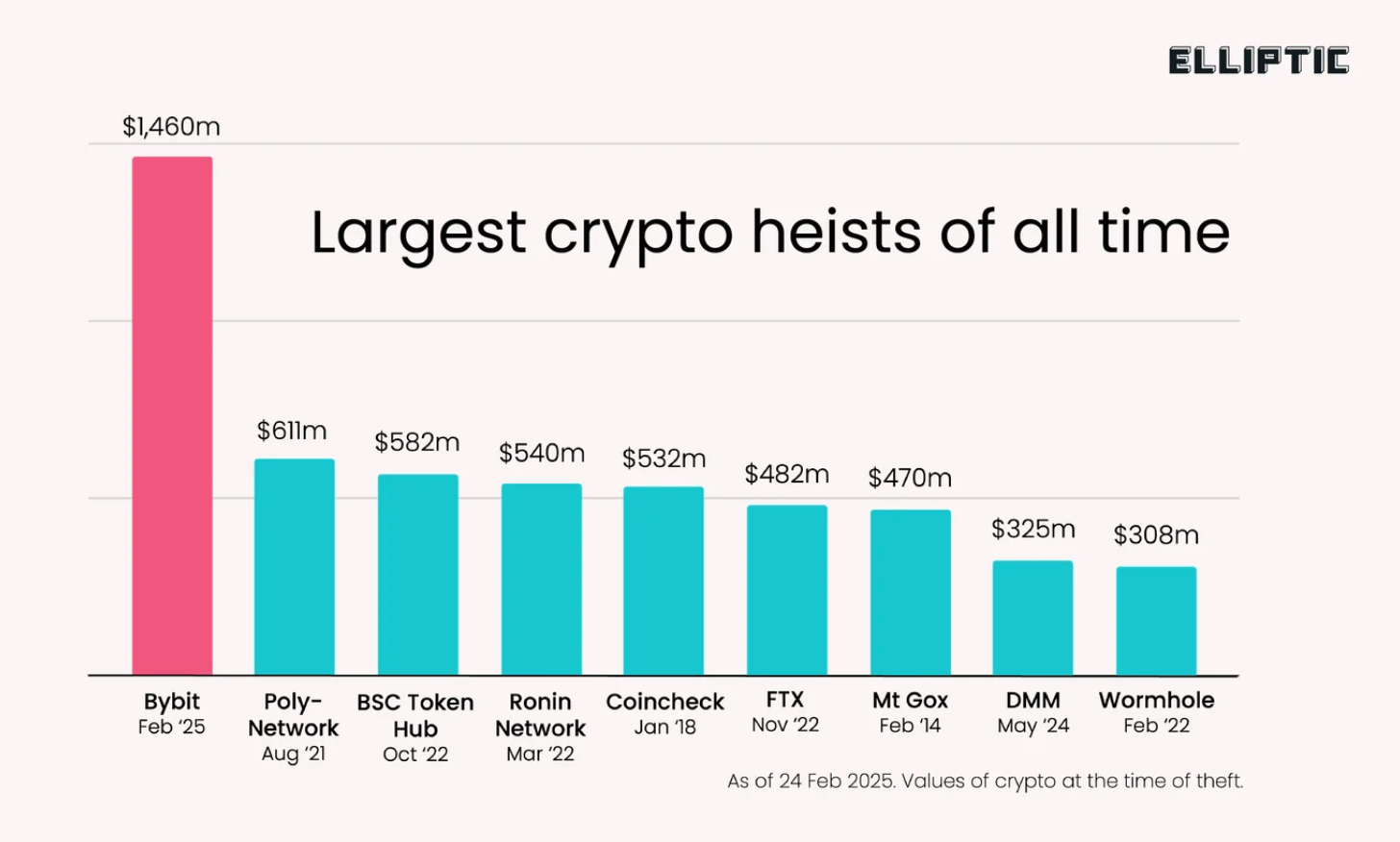
The crypto compliance firm Elliptic also backed up the attribution and wrote: "This is by the far the largest crypto heist of all time, dwarfing the $611 millionstolen from Poly Network in 2021 (and the vast majority of these funds were eventually returned by the hacker).
"In fact this incident is almost certainly the single largest known theft of any kind in all time, a record previously held by Saddam Hussein, who stole $1 billion from the Iraqi Central Bank on the eve of the 2003 Iraq War."
"North Korea-linked actors have stolen over $6 billion in cryptoassets since 2017, with the proceeds reportedly spent on the country’s ballistic missile program," it added.
How did the Lazurus Group launder the stolen crypto?
Elliptic's allegation was based on an analysis of the laundering of the stolen cryptoassets and other information.
Elliptic said Lazarus Group's laundering process "typically follows a characteristic pattern".
They reportedly started by converting stolen tokens into native blockchain assets like Ether or Bitcoin (BTC) because token issuers sometimes freeze wallets holding stolen tokens, while Ether and Bitcoin cannot be frozen by any central party.
In this case, attackers quickly swapped stolen tokens such as stETH and cmETH for Ether using decentralized exchanges (DEXs).
Lazarus is currently engaged in this second stage of laundering. Within two hours of the theft, the stolen funds were sent to 50 different wallets, each holding approximately 10,000 ETH. These are now being systematically emptied.
As of 1pm UTC on February 24, 14.5% of the stolen assets (now worth $195 million) have been moved from these wallets.
Once moved out of these wallets, the funds are being laundered through various services, including DEXs, cross-chain bridges and centralized exchanges," Elliptic continued.
"North Korea's Lazarus Group is the most sophisticated and well-resourced launderer of cryptoassets in existence, continually adapting its techniques to evade identification and seizure of stolen assets," Elliptic warned.
Have you got a story or insights to share? Get in touch and let us know.